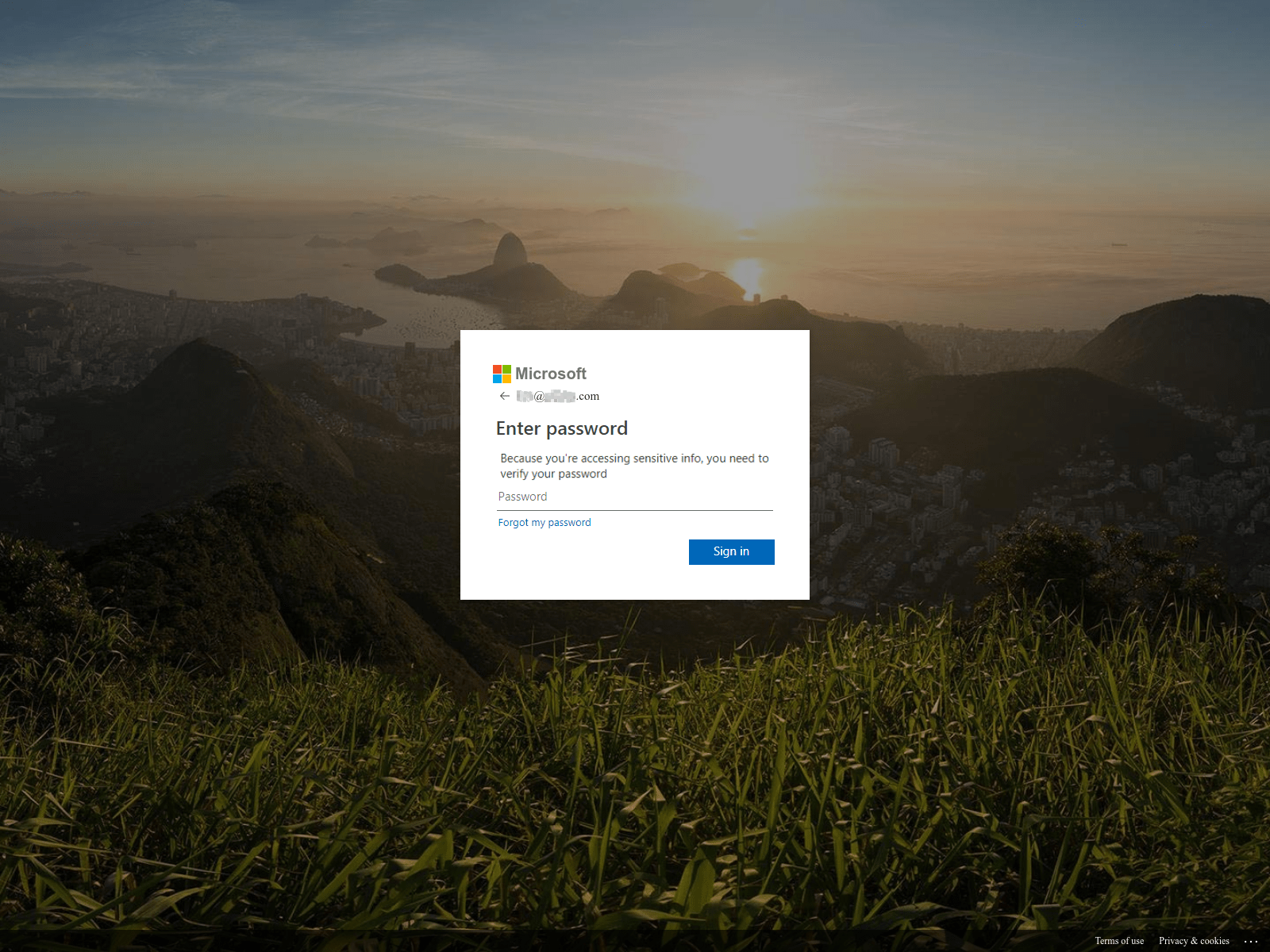
Many detection engines crawl websites and follow links to determine whether a website is malicious or masquerading as another. The difficulty threat actors face combatting these advanced technologies is that their phishing websites must bypass the detection engine, while simultaneously gaining a victim’s trust by displaying images and themes that mimic the targeted website.
WMC Global Threat Intelligence Team
Recent posts by WMC Global Threat Intelligence Team
2 min read
Office 365 Phishing Uses Image Inversion to Bypass Detection
By WMC Global Threat Intelligence Team on 11/4/20 9:00 AM
Topics: Phishing Microsoft Office 365 Image Inversion
4 min read
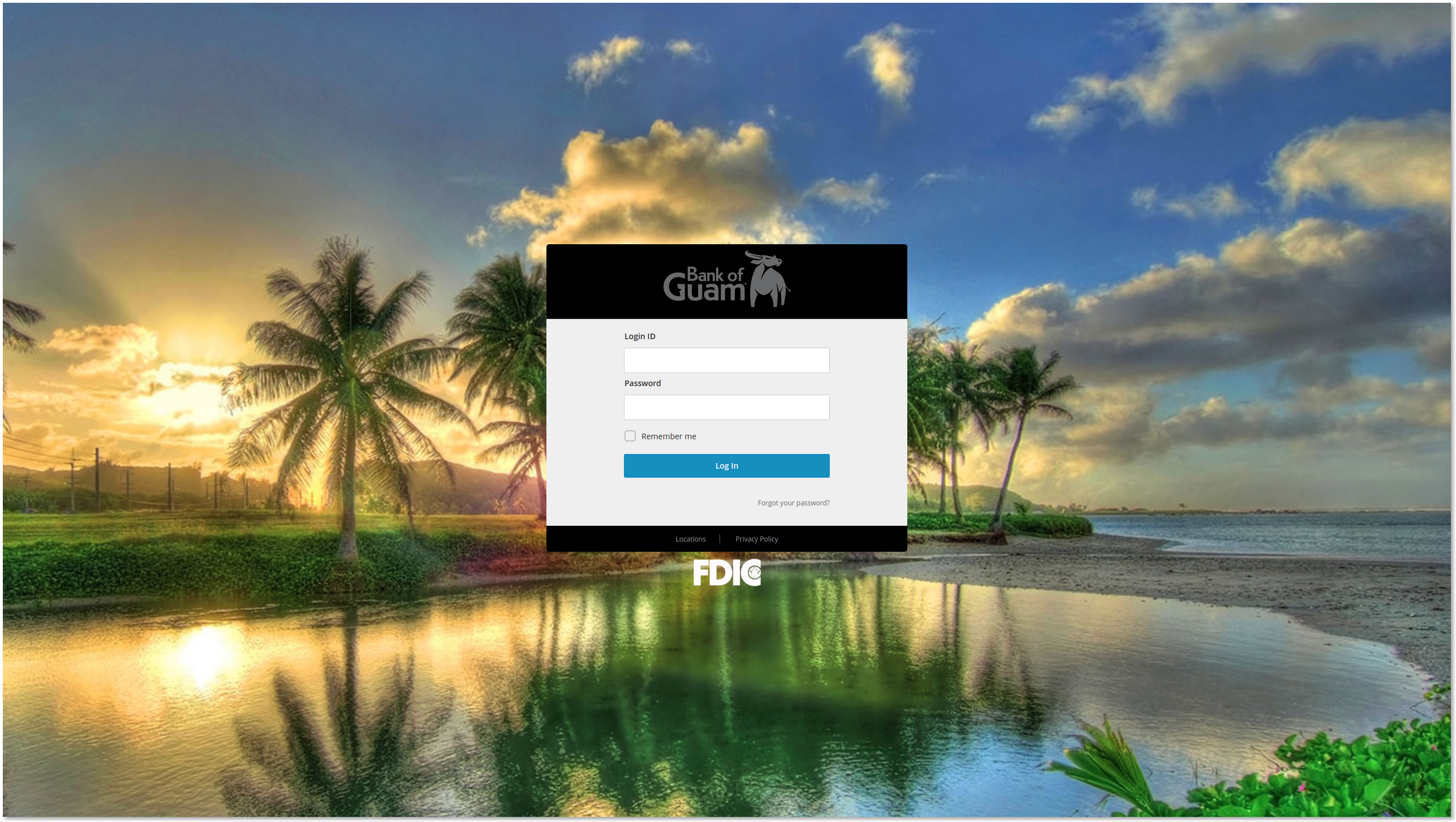
Bank of Guam Phishing Campaign Analysis
By WMC Global Threat Intelligence Team on 10/30/20 1:00 PM
Topics: Phishing Phishing Kit Banking 2FA Bank of Guam Two-Factor Authentication
9 min read
Netflix-Branded Mobile Phishing Campaigns in August
By WMC Global Threat Intelligence Team on 9/23/20 9:30 AM
Threat actors target a range of services often either due to credential resale value or to target higher value accounts in credential stuffing campaigns. Last month, WMC Global tracked three unique Netflix-branded phishing campaigns that resulted in over 390,000 unique URLs (Figure 1). These campaigns were solely distributed via text messages (SMS) to US mobile numbers. WMC Global’s analysis in the campaigns provides unparalleled visibility into Netflix-branded phishing attacks.
Topics: SMS Attack Phishing Phishing Kit Netflix
6 min read
Phishing Kit Exfiltration Methods
By WMC Global Threat Intelligence Team on 8/19/20 9:05 AM
At WMC Global, we analyze hundreds of phishing kits every week, which use a range of lures to steal credentials from victims, and we examine the exfiltration mechanisms used by threat actors to harvest stolen credentials from victims. The majority of phishing kits use a simple email exfiltration method to send victims’ data—compromised credentials—to a mailbox owned by the threat actor; the second most common method of exfiltration was writing the stolen data to a file stored on the website host. Though there are many exfiltration methods available to threat actors, our analysis found email and file write exfiltration to be amongst the most common.
Topics: Phishing Phishing Kit Data Exfiltration
4 min read
Cazanova Phisher Steals From Himself
By WMC Global Threat Intelligence Team on 8/14/20 10:30 AM
Using a variety of tools and techniques, WMC Global actively tracks threat actors engaged in credential phishing attacks—from canary detection to phishing site launch to the selling of compromised credentials, WMC Global monitors phishing activities the world over.
Topics: Phishing Phishing Kit Cazanova Phoenix Coder Threat Intel
3 min read
COVID Update
By WMC Global Threat Intelligence Team on 8/12/20 10:00 AM
Throughout the early months of the COVID-19 pandemic, when companies and consumers were forced to adapt to remote working arrangements and adopt digital interactions with family and friends to stay connected, PhishFeed witnessed a stark rise in phishing attacks, particularly in attacks configured to show only on mobile devices. Since January 2020, PhishFeed has collected tens of thousands of phishing URLs and kits, many of which were branded with COVID-themed domains, URLs, or attack content by the responsible threat actors, as seen in Figure 1.
Topics: Covid SMS Attack Phishing Covid-19
25 min read
Deep Dive Into Cazanova Morphine Phishing Kit
By WMC Global Threat Intelligence Team on 8/10/20 9:00 AM
WMC Global proactively tracks phishing sites and analyzes the backend code to understand tactics, techniques, and procedures (TTPs) used by threat actors to steal consumers' credentials and other personally identifiable information (PII) for financial gain.