This blog is released in partnership with Mobile Ecosystem Forum (MEF), of which WMC Global is a proud member.
WMC Global has noticed a sharp spike in phishing attacks targeting consumers using COVID-19 phishing lures. Specifically, these lures have impersonated US and UK government bodies, both locally and nationally. NHS-themed credential phishing attacks target UK consumers using lures linked to the NHS COVID-19 vaccine and a digital COVID vaccine passport. US threat actors use a slightly different approach, impersonating local and state governments by using state COVID-19 financial grants and benefits as lures. While these attackers are not part of the same cooperative, their choice in targets speaks to the disintegrating line between which established organizations can be considered trustworthy.
BACKGROUND
Threat actors often leverage current events and impersonate trusted entities such as public services and government offices. WMC Global has seen many COVID-19-themed phishing attacks since the start of the pandemic, as well as other ongoing topical lures surrounding yearly events like tax day, Amazon Prime Day, and Black Friday. However, impersonating a national health service and state governments providing financial grants during a global health crisis is a bold move, not only because these bodies are huge government entities, but also because they offer something deeply personal and a wide variety of people, regardless of demographic, trust them implicitly. These are intimate attacks that lead people to question what is now safe.
When threat actors use tax-themed lures to target small and medium sized businesses (SME), they are often targeting organizations that have limited resources to protect against cyber-attacks. When impersonating a nation’s health service, however, threat actors open up additional moral and ethical questions that come along with targeting every citizen of a country en masse. People typically accept that phishers will spoof their personal financial institutions, but the targeting of their healthcare in the midst of a global health crisis brings these threat actors to a new low.
Curiously, WMC Global has witnessed a surge of these phishing sites being stood up and then, all at once, a complete stop to the activities. We do not yet know why the sudden rise and fall of these themes has occurred, but we hypothesize that when a threat actor targets something as sensitive as COVID-19 vaccinations, they expect law enforcement to take a keen interest and choose to operate quickly and with dexterity.
NHS PHISHING ATTACKS
WMC Global captured a number of unique phishing kits used to create the NHS copycat sites, allowing our threat analysts to understand the websites’ code, and discover phishing victims’ email addresses linked to the sites.
Phishing kit analysis employing KITIntel shows that there are several unique kits used; however, there are still a very low number of kits deployed overall compared to the comparable financial themed phishing attack. Our researchers suspect the reason for this is due to either a large number of victims falling for each deployment, leaving controlling threat actors to spend longer handling victim logs before needing to set up new sites, or the speed of detection making it financially unviable for threat actors to run this campaign frequently.
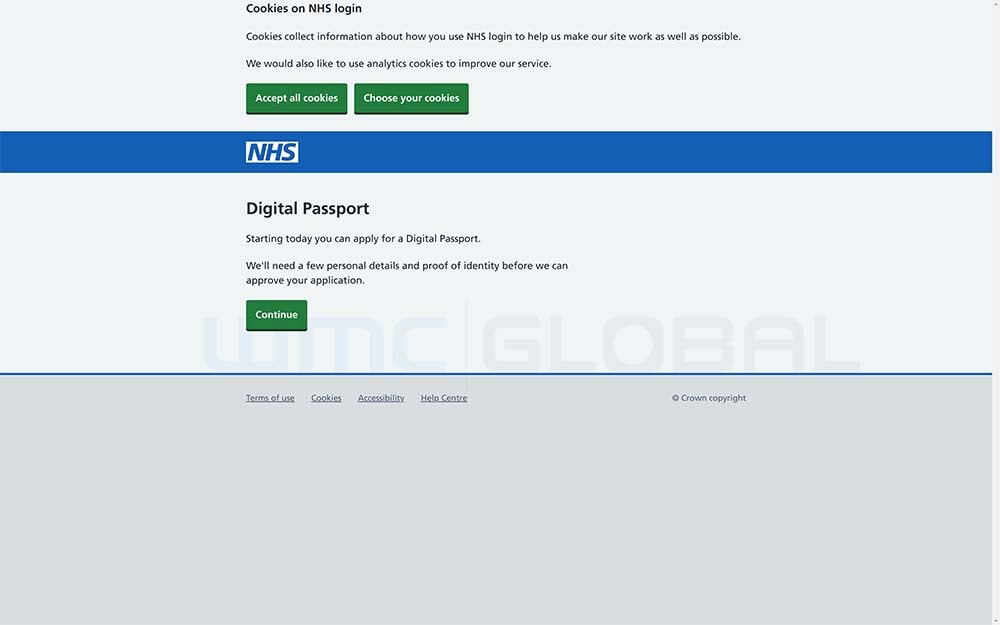
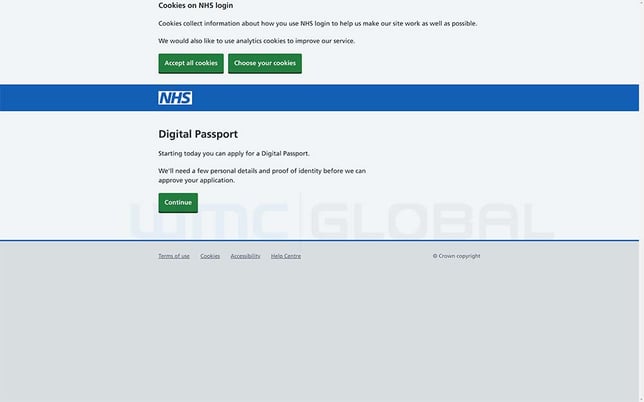 Figure 1: Spoofed NHS Digital Vaccine Passport Start Page
Figure 1: Spoofed NHS Digital Vaccine Passport Start Page
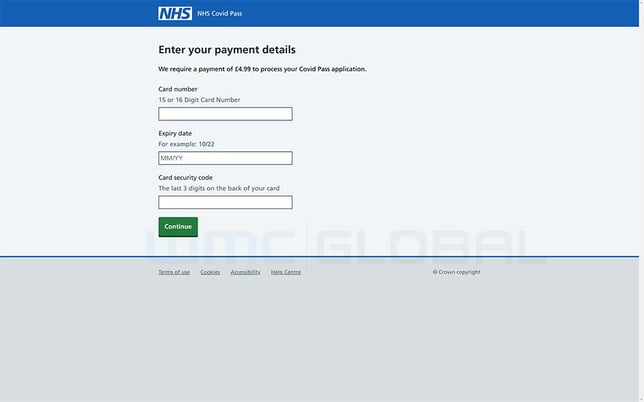 Figure 2: Spoofed NHS Digital Vaccine Passport Payment Details Page
Figure 2: Spoofed NHS Digital Vaccine Passport Payment Details Page
US LOCAL GOVERNMENT PHISHING ATTACKS
During the same period of time, WMC Global noticed US state government phishing campaigns being sent via SMS. These local government phishing sites used COVID-19 tax rebate and Covid-19 government grant lures, playing off Americans’ financial instability during the pandemic. Taking advantage of the disunity of state organizations, controlling threat actors use geographical targeting to achieve wide campaign, also ensuring every state has a realistic site featuring the state seal and correct verbiage. While this is a timely exercise for the actors, their investment suggests they get better results owing to the campaigns’ targeted nature.
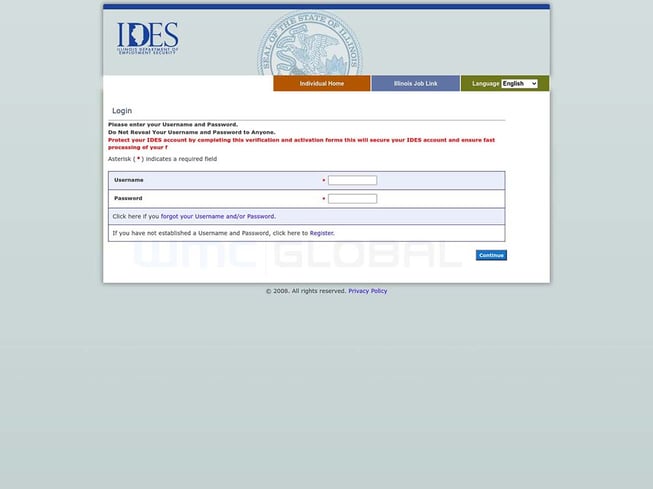 Figure 3: Spoofed Illinois Department of Employment Security (IDES) Login Page
Figure 3: Spoofed Illinois Department of Employment Security (IDES) Login Page
Owing to WMC Global’s particular visibility into phishing sites structure, including marked differences between the kits and code overlap, our researchers can identify that different threat actors are choosing to run similar campaigns globally.
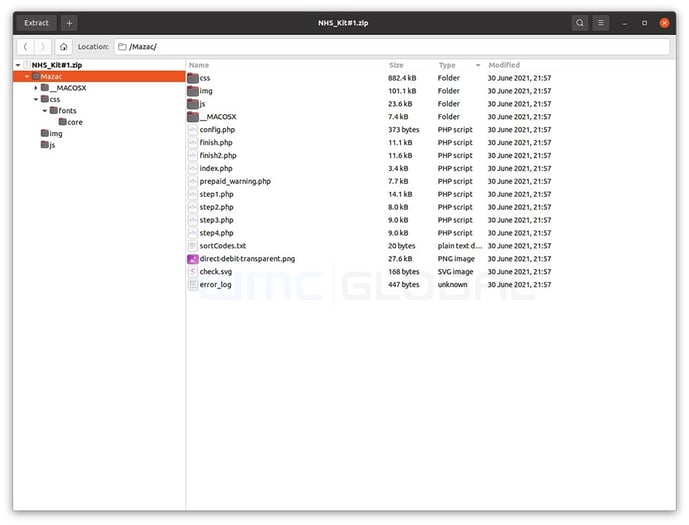 Figure 4: NHS Phishing Kit Files
Figure 4: NHS Phishing Kit Files
CONCLUSION
As the COVID-19 pandemic shows no signs of slowing, citizens are looking towards their governments for more support, guidance, and simply as authority figures. A global health event has not occurred at this scale during a technologically complex age, supplying a distinct opportunity for threat actors to exploit gaps and an emotionally volatile population.
WMC Global expects to continue see a surge in government-impersonating phishing attacks globally and a resurgence in NHS and state government campaigns in the UK and US. Given the unique and largely trusted position health services play in a world pandemic, and with a wider vaccine rollout across the globe, they have become the latest and most lucrative target which threat actors can exploit. Governments should be coordinating on these attacks, strengthening their security around key internal systems, and educating their citizens on the risks of phishing attacks impersonating government systems.