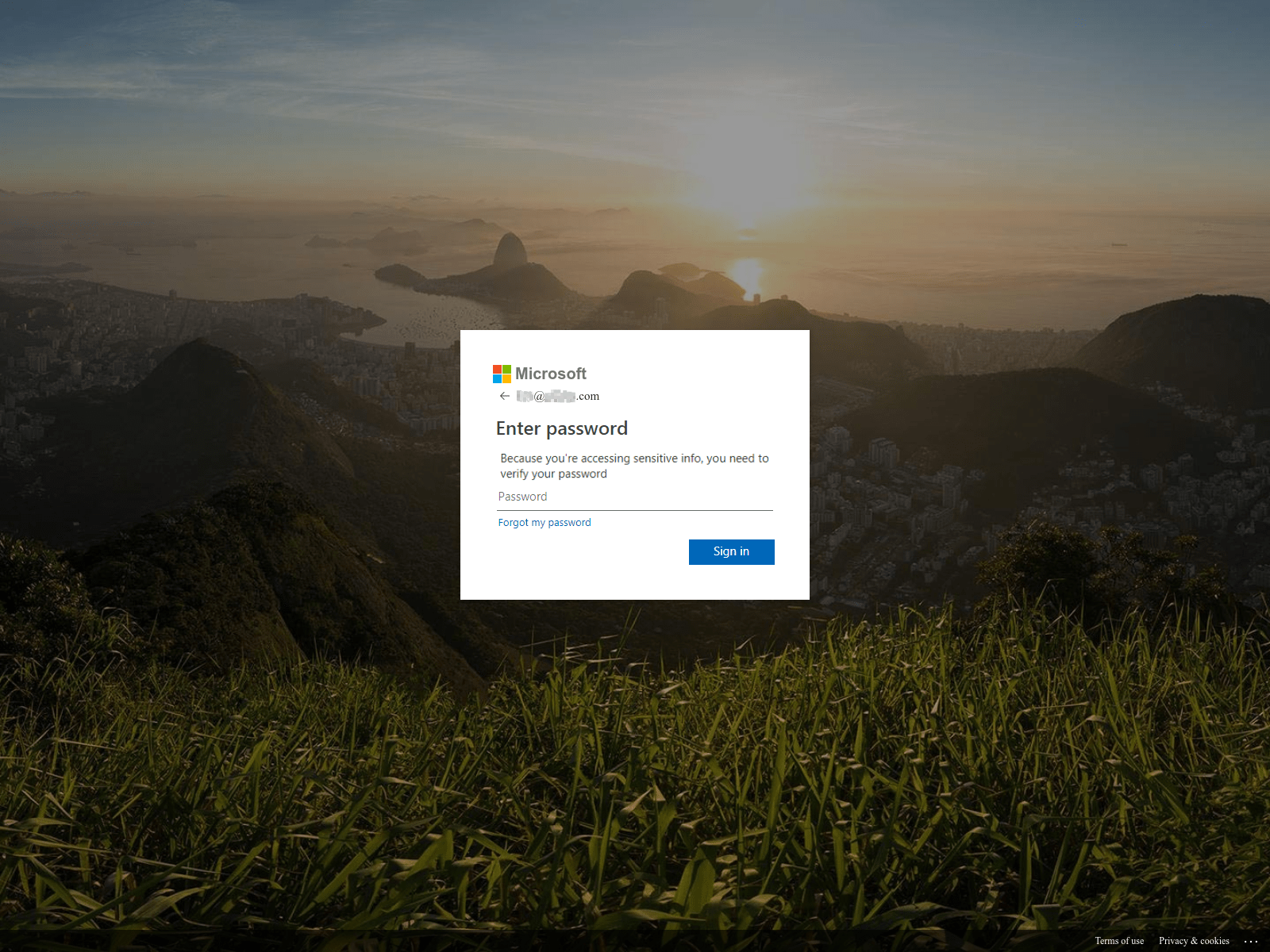
Many detection engines crawl websites and follow links to determine whether a website is malicious or masquerading as another. The difficulty threat actors face combatting these advanced technologies is that their phishing websites must bypass the detection engine, while simultaneously gaining a victim’s trust by displaying images and themes that mimic the targeted website.
2 min read
Office 365 Phishing Uses Image Inversion to Bypass Detection
By WMC Global Threat Intelligence Team on 11/4/20 9:00 AM