Summary
WMC Global's Threat Intel Team analyzed thousands of phishing kits in 2020. While "16Shop" continues to be the most popular, kits capable of capturing gathering multi-factor authentication data, like "Puppeteer," are emerging. There was a large increase in SMS phishing compared to emails over 2020, indicating SMS will continue to be a substantial threat in 2021. WMC Global observed that consumer brands continued to be the primary target for phishing, with Netflix and Facebook being the most impersonated brands; however, WMC Global also observed new threat vectors for phishing in the form of COVID-themed phishing. The United States was the number one location for hosting phishing sites, with NameCheap being the provider hosting the most phishing sites over 2020. WMC Global predicts that in 2021 multi-factor authentication will become a focus for threat actors, phishing link delivery methods will continue to evolve, and phishing kit intelligence will be more prevalent in tracking threat actors.
CONTENTS
Notable Phishing Attacks in 2020
- Covid-19 Themed Phishing Attacks
- Puppeteer Kit Attacks on UK Banks
- Netflix SMS Phishing Attacks
- Office 365 Image Inversion
- Top 10 Targeted Brands
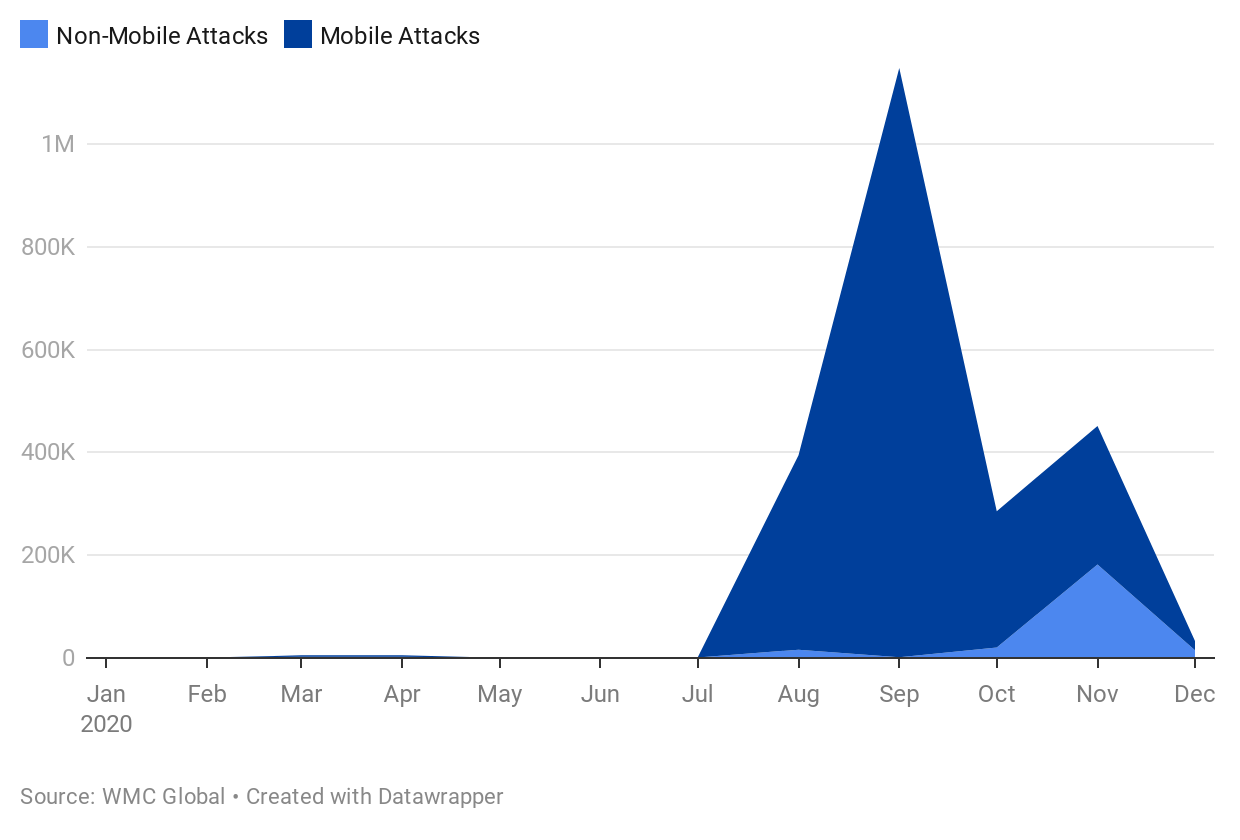
- Mobile (SMS) vs Non-Mobile Phishing Delivery
- Phishing Kits
- Top Kits by Brand / Name
- Top Hosting Locations
- Top Level Domain Trends
- Top Hosting Providers for Phishing
Introduction
2020 was a watershed year for both businesses and consumers. With COVID-19 forcing companies to shut their doors and implement work-from-home policies, threat actors saw an opportunity to exploit cybersecurity gaps with various types of phishing attacks. Throughout 2020 WMC Global saw increases in both traditional email phishing and newer forms of phishing, including SMS phishing (smishing), voice phishing (vishing), Puppeteer phishing kits stealing two-factor authentication codes, and more.
Notable Phishing Attacks in 2020
COVID-19 Themed Phishing Attacks
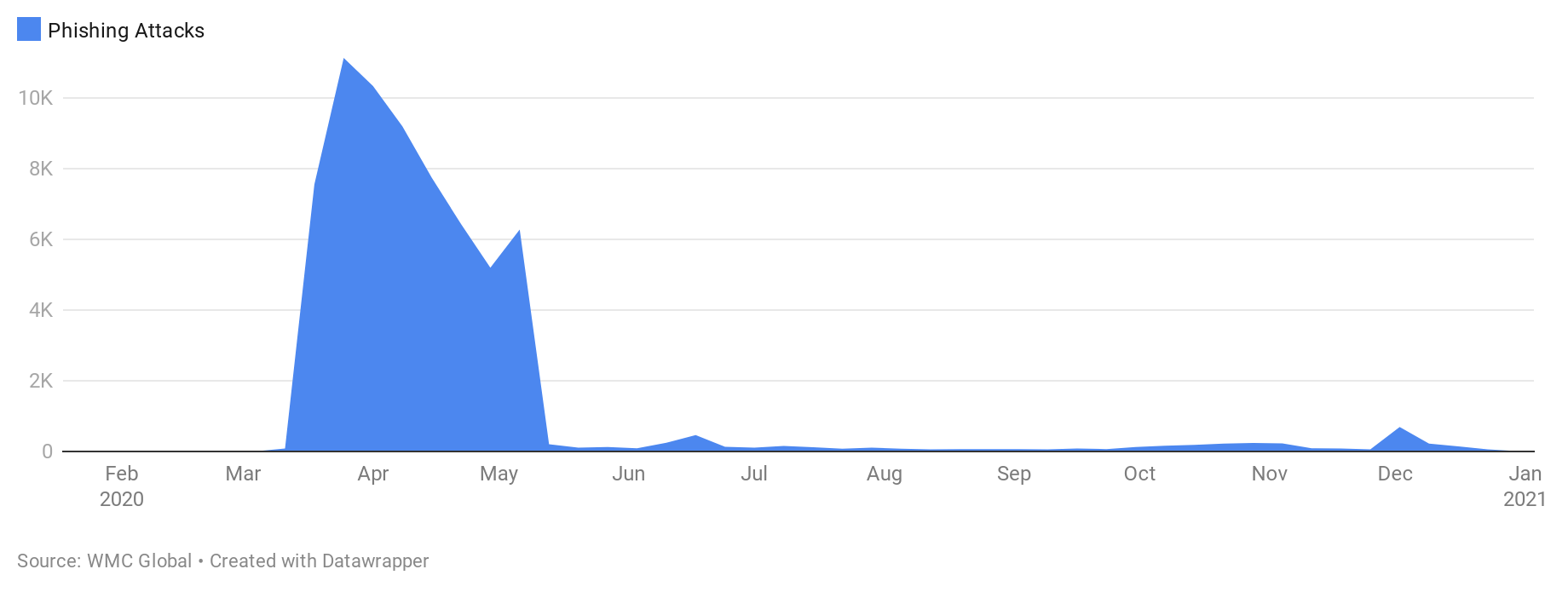
There was a massive surge in COVID-themed URLs, starting in January, which spiked in both March and April as most of the western world went into lockdown measures. The vast majority of these COVID-themed URLs contained credential phishing attacks that attempted to take advantage of employees working from home and the increased reliance on digital means of communication to conduct business and personal relationships.
WMC Global profiled these attacks in a July blog post.
As 2020 ended, we saw the largest vaccine roll-out in history. Countries bringing their national armies to support national health service deliver vaccines to as many people as possible. Threat actors capitalized on this good news, including surges in vaccine-based phishing attacks. We predict this trend will continue into 2021 as more vaccines are approved.
Puppeteer Kit Attacks on UK Banks
2020 saw the proliferation of the Puppeteer Kit. WMC Global detected Puppeteer Kits created by the threat actor named Kr3pto in July. These kits are dynamic and allow the threat actors to steal their victim's banking credentials, security codes, and two-factor authentication data. These kits impersonated a variety of financial institutions, including HSBC and Halifax.
WMC Global profiled Puppeteer Kits in a December blog post.
Netflix SMS Phishing Attacks
WMC Global tracked three massive Netflix-branded phishing campaigns that resulted in over 390,000 unique URLs targeted victims in the United States. These campaigns, which began in early August and lasted through September, used a Netflix lure and SMS messages warning recipients of a fake payment error on their account, requesting them to re-enter their credit card information.
We profiled these attacks in a September blog post.
Office 365 Image Inversion

In November, WMC Global discovered a new method that the threat actor, known as "Ex-Robotos," implemented to avoid phishing detection. Ex-Robotos created an Office 365 credential phishing site that attempted to bypass detection by inverting the colors of the images used on the site, causing them to differ from the original images and go undetected by image recognition detection programs.
We profiled these types of phishing websites in a blog post in November.
2020 Trends
Top Ten Targeted Brands
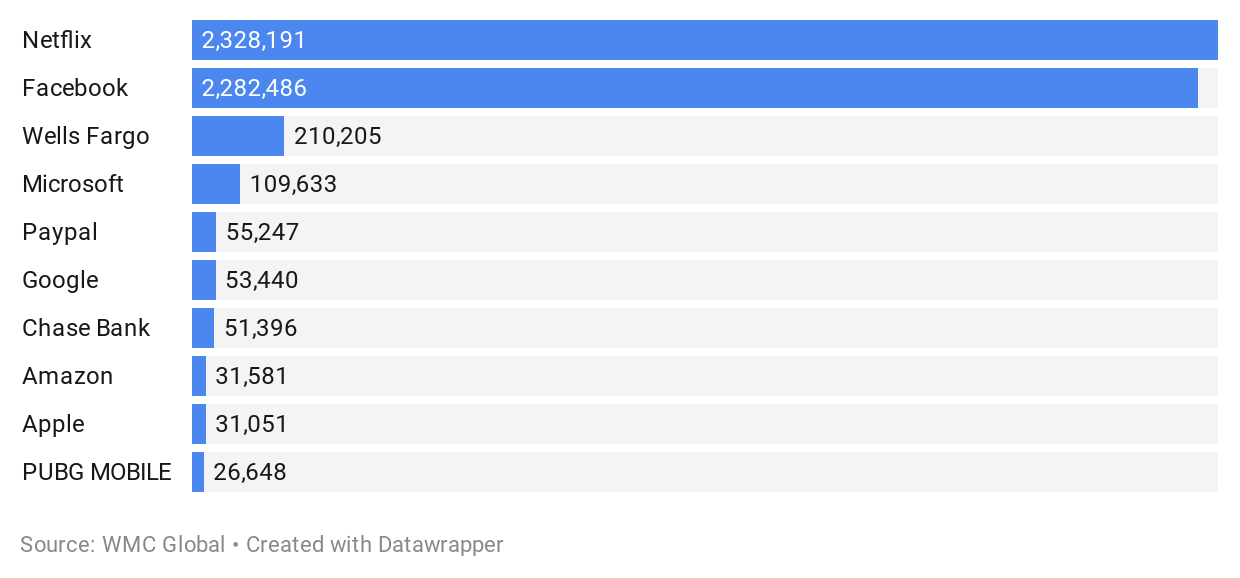

1. Netflix
Phishing attacks impersonating Netflix have been rising in recent years. At the beginning of 2020, WMC Global detected roughly 5k-10k Netflix-branded URLs a month until August, when a large SMS based smishing attack began and continued through September.
This attack targeted Netflix customers with fake text messages, telling them that there was a payment error on their account, and directing them to a phony login and payments page to re-enter their credit card information.

2. Facebook
With over 2.7 billion monthly active users, Facebook is one of the most popular websites globally, making it a popular brand to impersonate in phishing attacks. In Q4 of 2020, we identified several distinct Facebook phishing campaigns targeting victims via both SMS and more traditional methods, such as email. The campaigns were unique in their size compared to the rest of the year.
Facebook phishing scams commonly use social engineering to scare or entice users to enter their credentials on the fake Facebook page. Common scams include "confirm your account" messages, "account abuse warning" messages, and credit card harvesting scams. Once compromised, a Facebook account is typically used to launch further phishing attacks by impersonating the compromised account owner which can cause accounts to become banned by Facebook or threat actors often also steal personal identifiable information of the user.

3. Wells Fargo
WMC Global saw an increase in SMS phishing, including a large SMS attack in August using Wells Fargo as a lure. Wells Fargo was the third most impersonated brand in 2020. Scams impersonating financial institutions often take the form of fake security alerts, tricking customers into logging into a phony banking website by sending them an email or SMS alert saying that there was a fraudulent login on their account.

As one of the world's largest companies, Microsoft brand impersonation remained steady throughout the year in phishing attacks. One notable phishing kit detected this year was the Microsoft Office 365 phishing kit "Morphine" created by threat actor "Cazanova Haxor," that WMC profiled in a blog post earlier this year.

PayPal continues to be one of the most impersonated brands in phishing attacks. WMC Global profiled several PayPal phishing kits this year, including a kit by threat actor “ShadowZ118” and “16Shop” kits also target PayPal. As a result of the profiling our Threat Analsts are able to track these campaigns closely, commenting on changes in TTPs.

Chase Bank was the second most targeted financial institution in 2020, after Wells Fargo. We saw phishing attacks sent through SMS using Chase Bank as a lure every other month which caused very notable spikes and troughs in data attributed to Chase Bank over the year.
Banks are a very popular target for phishing lures due to the immediate payout that stolen banking credentials provide.

Google phishing attacks spiked in Q4 of 2020, targeting the Google One platform. Google accounts are valuable targets for threat actors due to the amount of data accessible by a user. Threat actors target Google credentials to access the victim's email, documents, contacts, Pay Send, and other linked accounts.
WMC Global predicts a notable rise in Google phishing lures given the continued adoption by businesses to use the platform.

Amazon has been a prime target for phishing attacks for years. Despite a small spike in Q4, Amazon attacks remained relatively stable throughout the year. Amazon accounts are a popular target for cybercriminals due to the ease of cashing out once they have compromised an account. Amazon phishing scams commonly take the form of email or SMS messages requesting the victim to update their billing information or resolve an issue with a fake order.

Apple IDs were a common target in 2020. Due to iPhones and MacBooks generally having excellent security, phishing can be one of the only ways to get Apple credentials, making Apple IDs a perennial popular target for phishing scams.

Popular video game PUBG is a unique target. Through enhanced tracking of this threat in Q4, WMC Global discovered a considerable trove of PUBG phishing attacks attributed to Indonesian threat actors. The Asian phishing landscape frequently uses covers for phishing while targeting more generic credentials. For example, PUBG phishing will lure the victim, but it is ultimately Facebook credentials requested by the phishing site.
Mobile (SMS) vs Non-Mobile Phishing Delivery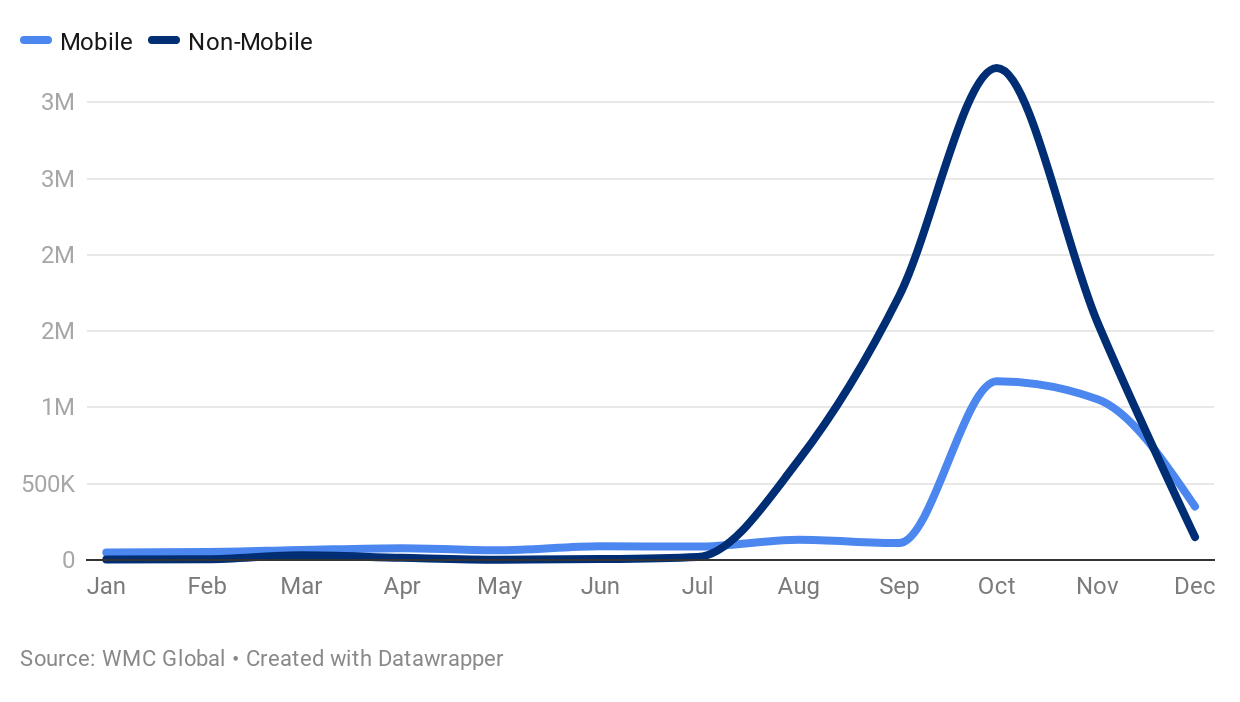
WMC Global's anti-phishing product suite provides unique insight into SMS phishing through our working relationship with major telecommunication companies and access to thousands of SMS honeypots located around the globe. These relationships allow a global view of the SMS phishing (or smishing) landscape globally.
Although smishing has been around since at least the mid-2000s, it is becoming increasingly common in recent years. With enterprises investing in securing their networks and educating their employees on phishing, smishing can bypass cyber-security platforms and slip under the radar, making it very appealing to threat actors. An SMS can avoid protection methods to deliver phishing directly to the user collecting the user's password, two-factor authentication code, or other private information.
PHISHING KITS
A phishing kit is a phishing software package that attackers can use with little to no technical skills to launch phishing attacks. A phishing kit typically includes website and email templates that imitate a legitimate company and a back-end component to exfiltrate stolen data. Some kits include lists of emails and phone numbers to target.
WMC Global detects, catalogs, and analyzes phishing kits, breaking down how they work, how they exfiltrate stolen data, and attributing them to threat actor groups. For more information on phishing kit exfiltration methods, see this blog post.
Top Kits by Brand/Name
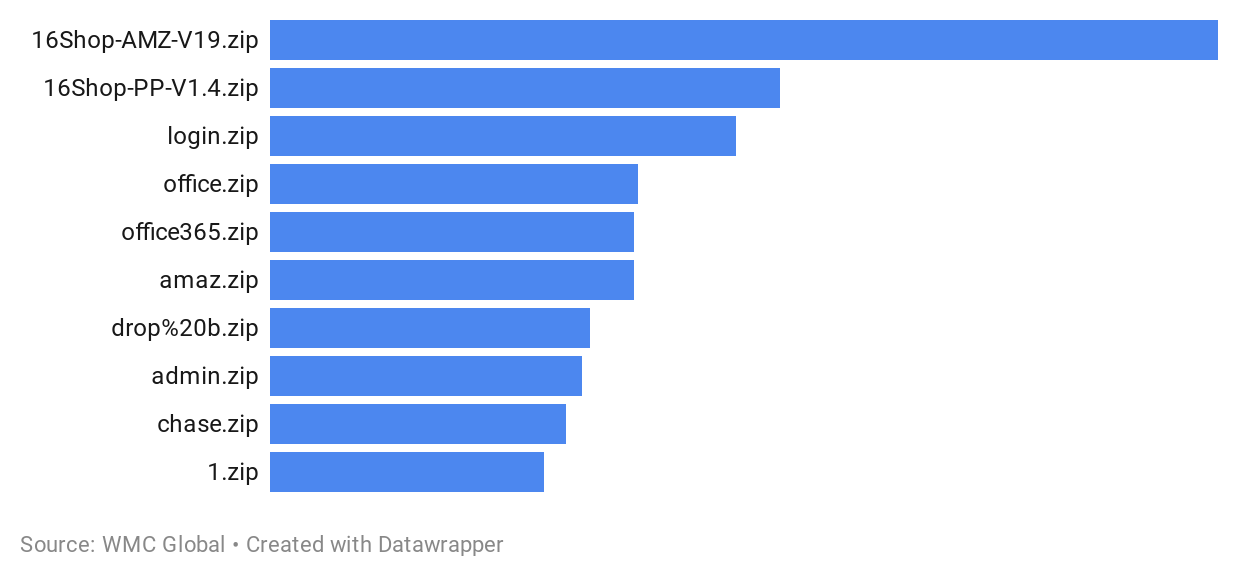
First detected in late 2018, 16shop kits, created by a cyber-criminal group known as the "Indonesian Cyber Army", initially targeted Apple accounts in the US and Japan before expanding to other brands and countries. In 2020 16Shop is the most commonly detected Phishing Kits, targeting Amazon and PayPal.
- 16Shop-AMZ-V19.zip
- 16Shop-PP-V1.4.zip
- Login.zip
- Office365.zip
- Office.zip
- drop%20b.zip
- Amaz.zip
- Chase.zip
- Admin.zip
- excelz.zip
Over 2020 we collected more kits created by 16Shop targeting Amazon and PayPal than any other kit. Other common phishing kits included Office365.zip, Office.zip, and excelz.zip, targeting Microsoft Office users, Dropbox, and Chase Bank kits were also very commonly found online.
Top Hosting Locations
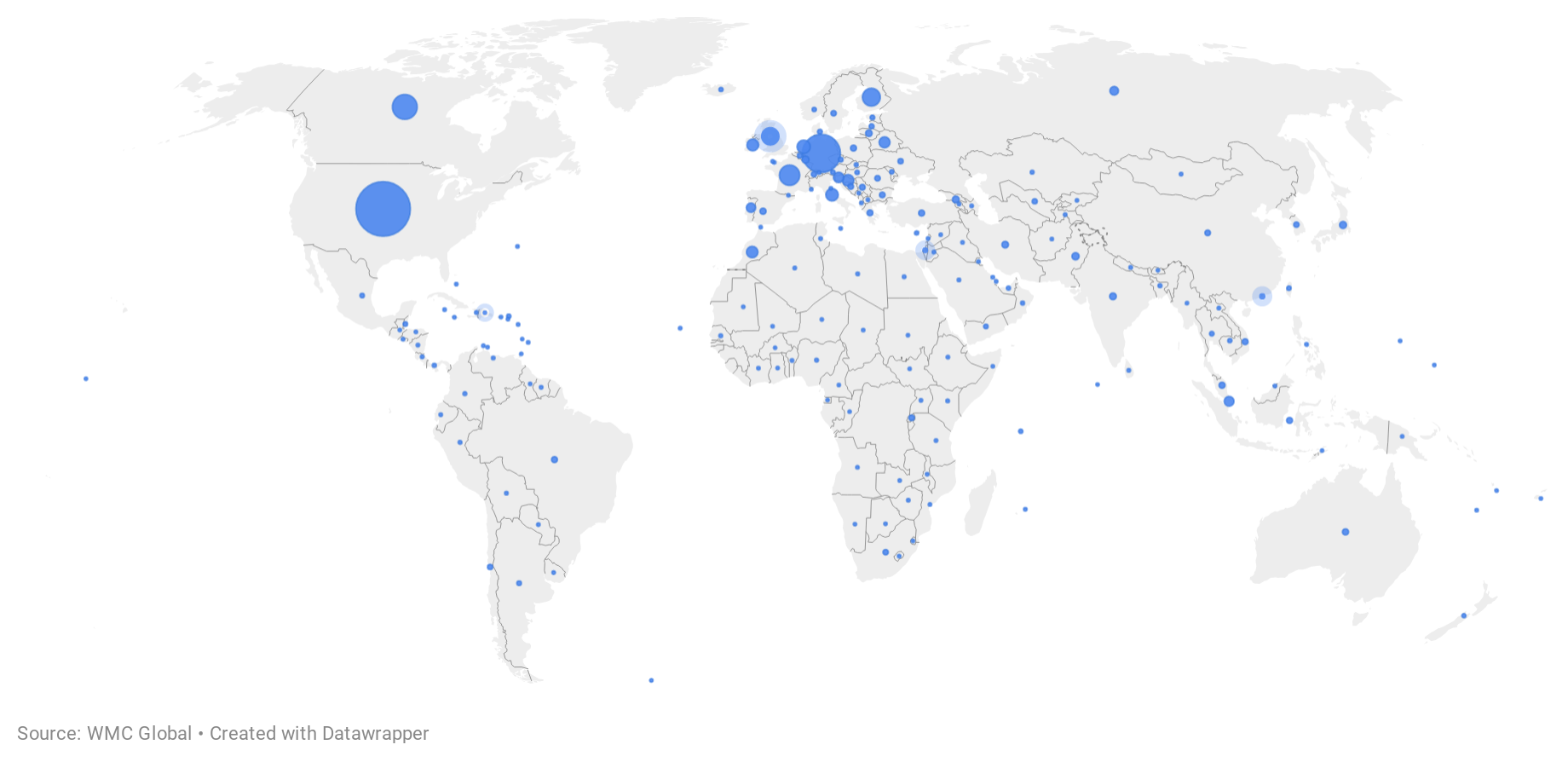
Phishing is a global issue, but some countries see many more hosted phishing sites than others. The top five countries for hosting phishing sites are listed below, with the United States having more than double the number of phishing sites as the second-ranked country, Germany.
- United States
- Germany
- Canada
- France
- United Kingdom
Top Level Domain Trends
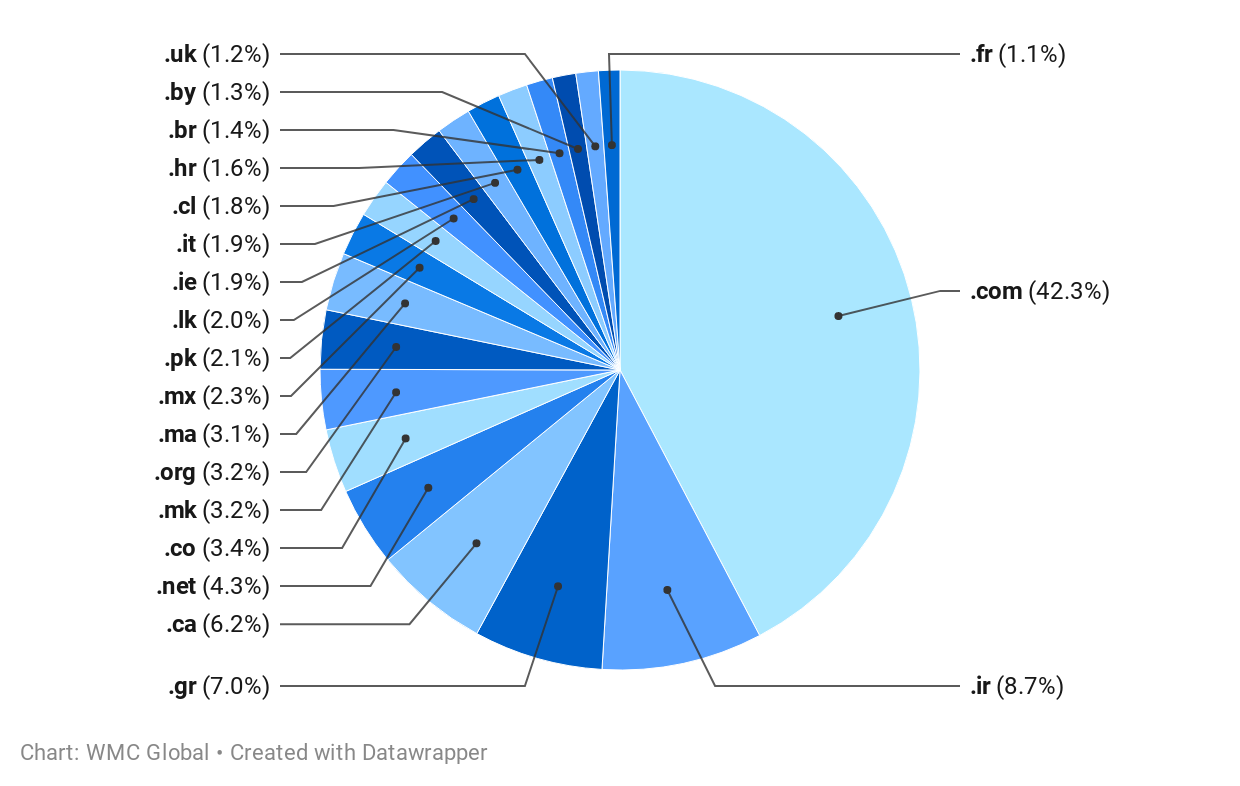
Top Level Domains (TLDs) such as ".com" and ".net" host large numbers of phishing websites. ".com" in particular hosted the most phishing sites this year. There are several contributing factors, including that threat actors typically prefer ".com" domains because they are common, and therefore less likely to arouse suspicion in the victim. Additionally, many phishing websites compromise legitimate domains, which frequently utilize more popular TLDs.
Top Hosting Providers for Phishing
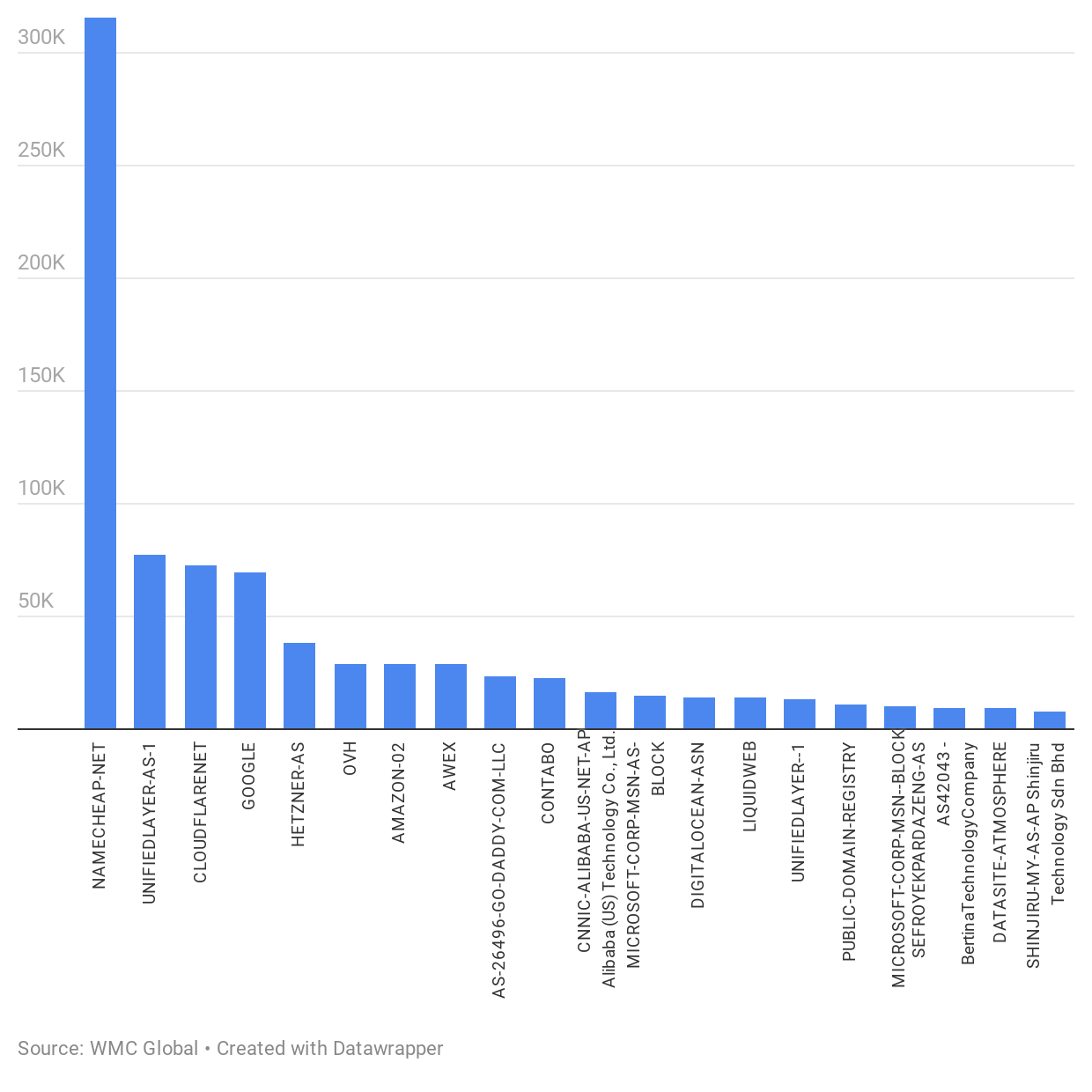
In recent years, hosting providers are becoming more active in taking down phishing sites and taking steps to reduce phishing on their platforms. However, threat actors deploying phishing sites on a wide range of hosts. The hosting providers that hosted the most phishing sites in 2020 are:
- NameCheap
- Endurance International Group
- CloudFlare
- Hetzner Online GmbH
Phishing websites hosted by these providers include both paid phishing sites, which have been purchased by the threat actor, and legitimate sites that have been compromised and used to host phishing content.
2021 Outlook
As 2021 continues, WMC Global threat analysts assert that Multi-factor bypassing, delivery method TTPs (Tactics, Techniques, and Procedures), and phishing kits analysis will pose the most significant changes to the phishing industry in 2021.
Multi-Factor (MFA / 2FA) Bypassing
With the proliferation of security threats, multi-factor authentication is becoming increasingly common. Today, most applications require at least two forms of authentication; password, security code via email, SMS, or authentication app. 2FA helps prevent fraudulent logins.
In 2020, WMC Global saw a surge in kits that allow threat actors to adapt their phishing pages to individual victims' login processes. Known as Puppeteer Kits or Live Kits, these types of phishing kits are highly valuable because they allow the threat actor to steal their victim's credentials and the 2FA codes needed to access their account. The growing emergence of these kits mean 2FA is not enough to keep an account secure from this type of attack.
New Delivery Methods – WhatsApp, Teams, SMS, Voice
While phishing is typically considered an email-based threat, phishing attacks are increasing via other means. Phishing SMS and voice delivery are becoming increasingly common. Email providers and other organizations dedicate significant resources to filtering and fighting phishing lures, making it more difficult for threat actors to steal credentials. With the rise in remote working, threat actors have started to focus on other delivery methods. WMC Global predicts an increase in delivery methods using SMS, voice, and compromised accounts will continue to increase, given this delivery method's success in avoiding countermeasures put in place on email systems. We also expect new delivery methods will emerge in communication platforms such as Microsoft Teams, WhatsApp, and Slack to deliver phishing links.





