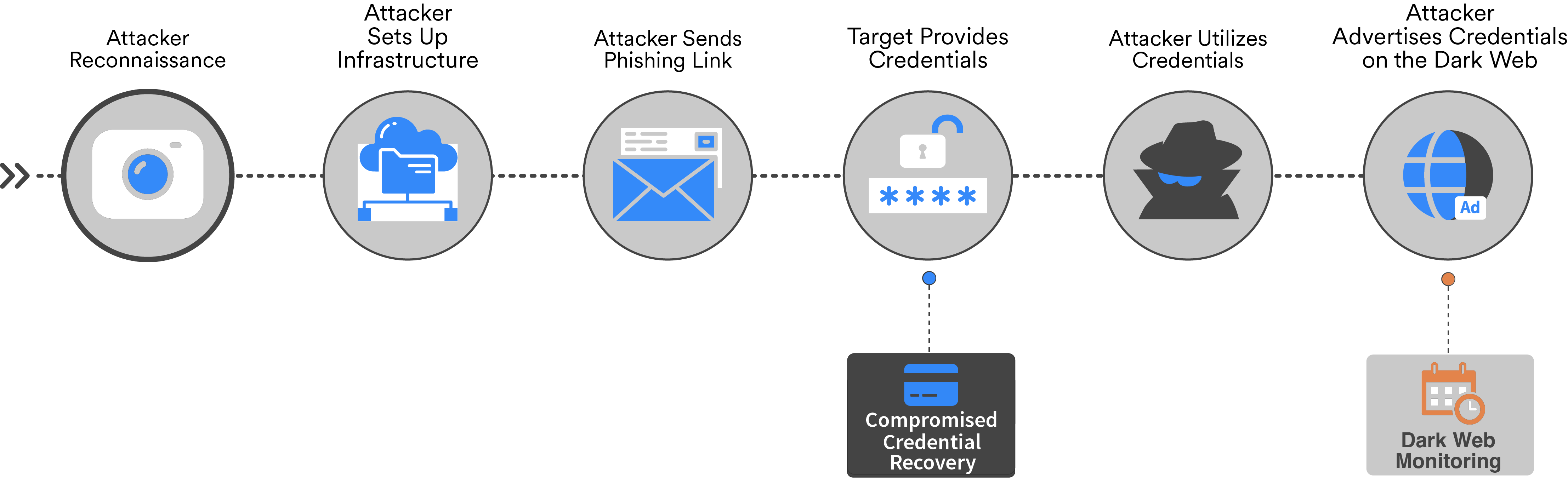
In reality, weeks, months, or years can pass before victim credentials become available on the Dark Web, rendering common monitoring services ineffective at offering visibility into the attack and threat actor behind it. This often leaves businesses bereft of an immediate solution and playing whack-a-mole with threat actors. Compromised Credential Recovery's unique data, however, comes from neither breaches nor the Dark Web. WMC Global locates compromised data at first exposure in phishing attacks and transfers it back to you via secure API, actively preventing account takeover.
Law enforcement often struggles to correlate data from disparate sources. Go on the offensive to support their efforts with forensic evidence. Attributing specific campaigns to the impacted victims and losses enables law enforcement to take action against threat actors affecting your business.
Shine a light on what's happening during live campaigns. Obtain a deeper understanding of threat actor tactics, techniques, and procedures (TTPs). Gain visibility into the exfiltrated data on unmonitored devices (BYOD) and networks, augmenting existing controls.
Connect downstream systems to automate preventative actions. Our API integrates seamlessly with identity and authorization systems to streamline anti-fraud measures like password reset, so security teams never have to worry about attack repercussions.
Not all victims will make themselves known. Obtain a detailed picture of the true impact of each campaign by understanding what was stolen and quantifying potential and material losses.

Identify credentials that are insecure in either transit or storage.

Classify compromise hours before a fraud attempt takes place.
Collect the compromised data at scale from live phishing campaigns as it’s being collected by the scammer.

Make the data immediately available to our clients to minimize risk of additional exposure.

Plug into the API for delivery on your schedule or request a direct transfer on premises.